mirror of
https://github.com/jumpserver/jumpserver.git
synced 2025-12-16 00:52:41 +00:00
Compare commits
19 Commits
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
dd50a1faff | ||
|
|
86dab4fc6e | ||
|
|
a85a80a945 | ||
|
|
349edc10aa | ||
|
|
44918e3cb5 | ||
|
|
9a2f6c0d70 | ||
|
|
934969a8f1 | ||
|
|
57162c1628 | ||
|
|
32fb36867f | ||
|
|
158b589028 | ||
|
|
d64277353c | ||
|
|
bff6f397ce | ||
|
|
0ad461a804 | ||
|
|
a1dcef0ba0 | ||
|
|
dbb1ee3a75 | ||
|
|
d6bd207a17 | ||
|
|
e69ba27ff4 | ||
|
|
adbe7c07c6 | ||
|
|
d1eacf53d4 |
8
.github/ISSUE_TEMPLATE/bug---.md
vendored
8
.github/ISSUE_TEMPLATE/bug---.md
vendored
@@ -7,7 +7,7 @@ assignees: wojiushixiaobai
|
||||
|
||||
---
|
||||
|
||||
**JumpServer 版本( v2.28 之前的版本不再支持 )**
|
||||
**JumpServer 版本(v1.5.9以下不再支持)**
|
||||
|
||||
|
||||
**浏览器版本**
|
||||
@@ -17,6 +17,6 @@ assignees: wojiushixiaobai
|
||||
|
||||
|
||||
**Bug 重现步骤(有截图更好)**
|
||||
1.
|
||||
2.
|
||||
3.
|
||||
1.
|
||||
2.
|
||||
3.
|
||||
|
||||
1
.github/workflows/jms-build-test.yml
vendored
1
.github/workflows/jms-build-test.yml
vendored
@@ -24,7 +24,6 @@ jobs:
|
||||
build-args: |
|
||||
APT_MIRROR=http://deb.debian.org
|
||||
PIP_MIRROR=https://pypi.org/simple
|
||||
PIP_JMS_MIRROR=https://pypi.org/simple
|
||||
cache-from: type=gha
|
||||
cache-to: type=gha,mode=max
|
||||
|
||||
|
||||
2
.github/workflows/sync-gitee.yml
vendored
2
.github/workflows/sync-gitee.yml
vendored
@@ -20,4 +20,4 @@ jobs:
|
||||
SSH_PRIVATE_KEY: ${{ secrets.GITEE_SSH_PRIVATE_KEY }}
|
||||
with:
|
||||
source-repo: 'git@github.com:jumpserver/jumpserver.git'
|
||||
destination-repo: 'git@gitee.com:fit2cloud-feizhiyun/JumpServer.git'
|
||||
destination-repo: 'git@gitee.com:jumpserver/jumpserver.git'
|
||||
|
||||
16
README.md
16
README.md
@@ -10,17 +10,6 @@
|
||||
<a href="https://github.com/jumpserver/jumpserver"><img src="https://img.shields.io/github/stars/jumpserver/jumpserver?color=%231890FF&style=flat-square" alt="Stars"></a>
|
||||
</p>
|
||||
|
||||
|
||||
<p align="center">
|
||||
JumpServer <a href="https://github.com/jumpserver/jumpserver/releases/tag/v3.0.0">v3.0</a> 正式发布。
|
||||
<br>
|
||||
9 年时间,倾情投入,用心做好一款开源堡垒机。
|
||||
</p>
|
||||
|
||||
| :warning: 注意 :warning: |
|
||||
|:-------------------------------------------------------------------------------------------------------------------------:|
|
||||
| 3.0 架构上和 2.0 变化较大,建议全新安装一套环境来体验。如需升级,请务必升级前进行备份,并[查阅文档](https://kb.fit2cloud.com/?p=06638d69-f109-4333-b5bf-65b17b297ed9) |
|
||||
|
||||
--------------------------
|
||||
|
||||
JumpServer 是广受欢迎的开源堡垒机,是符合 4A 规范的专业运维安全审计系统。
|
||||
@@ -38,7 +27,7 @@ JumpServer 是广受欢迎的开源堡垒机,是符合 4A 规范的专业运
|
||||
|
||||
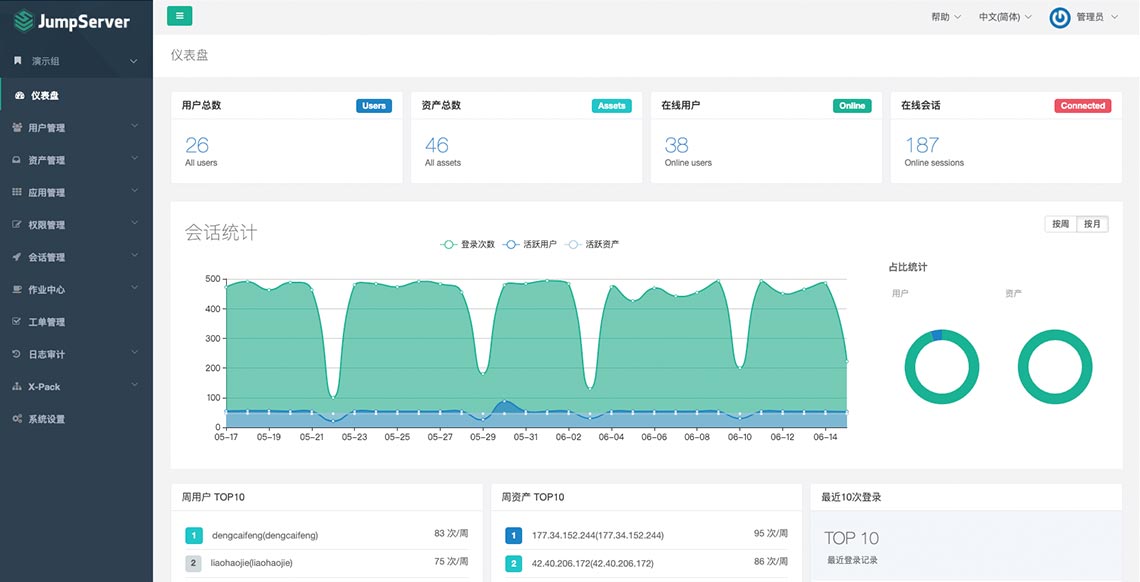
## UI 展示
|
||||
|
||||
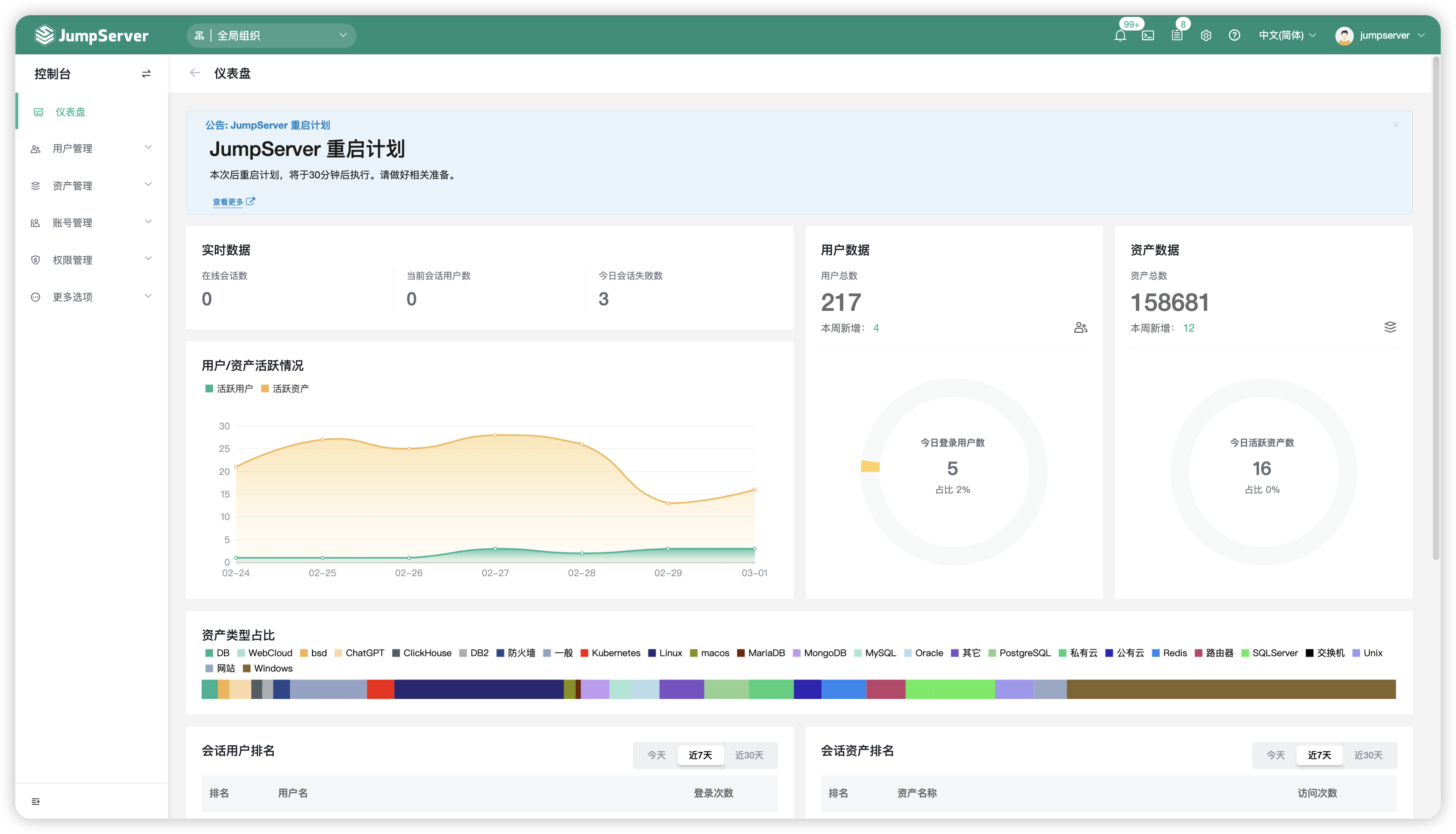
|
||||
|
||||
|
||||
## 在线体验
|
||||
|
||||
@@ -52,7 +41,8 @@ JumpServer 是广受欢迎的开源堡垒机,是符合 4A 规范的专业运
|
||||
|
||||
## 快速开始
|
||||
|
||||
- [快速入门](https://docs.jumpserver.org/zh/v3/quick_start/)
|
||||
- [极速安装](https://docs.jumpserver.org/zh/master/install/setup_by_fast/)
|
||||
- [手动安装](https://github.com/jumpserver/installer)
|
||||
- [产品文档](https://docs.jumpserver.org)
|
||||
- [知识库](https://kb.fit2cloud.com/categories/jumpserver)
|
||||
|
||||
|
||||
@@ -43,7 +43,7 @@ class AccountViewSet(OrgBulkModelViewSet):
|
||||
asset = get_object_or_404(Asset, pk=asset_id)
|
||||
accounts = asset.accounts.all()
|
||||
else:
|
||||
accounts = Account.objects.none()
|
||||
accounts = []
|
||||
accounts = self.filter_queryset(accounts)
|
||||
serializer = serializers.AccountSerializer(accounts, many=True)
|
||||
return Response(data=serializer.data)
|
||||
|
||||
@@ -1,39 +1,15 @@
|
||||
from django_filters import rest_framework as drf_filters
|
||||
|
||||
from assets.const import Protocol
|
||||
from accounts import serializers
|
||||
from accounts.models import AccountTemplate
|
||||
from orgs.mixins.api import OrgBulkModelViewSet
|
||||
from rbac.permissions import RBACPermission
|
||||
from common.permissions import UserConfirmation, ConfirmType
|
||||
|
||||
from common.views.mixins import RecordViewLogMixin
|
||||
from common.drf.filters import BaseFilterSet
|
||||
|
||||
|
||||
class AccountTemplateFilterSet(BaseFilterSet):
|
||||
protocols = drf_filters.CharFilter(method='filter_protocols')
|
||||
|
||||
class Meta:
|
||||
model = AccountTemplate
|
||||
fields = ('username', 'name')
|
||||
|
||||
@staticmethod
|
||||
def filter_protocols(queryset, name, value):
|
||||
secret_types = set()
|
||||
protocols = value.split(',')
|
||||
protocol_secret_type_map = Protocol.settings()
|
||||
for p in protocols:
|
||||
if p not in protocol_secret_type_map:
|
||||
continue
|
||||
_st = protocol_secret_type_map[p].get('secret_types', [])
|
||||
secret_types.update(_st)
|
||||
queryset = queryset.filter(secret_type__in=secret_types)
|
||||
return queryset
|
||||
from orgs.mixins.api import OrgBulkModelViewSet
|
||||
from accounts import serializers
|
||||
from accounts.models import AccountTemplate
|
||||
|
||||
|
||||
class AccountTemplateViewSet(OrgBulkModelViewSet):
|
||||
model = AccountTemplate
|
||||
filterset_class = AccountTemplateFilterSet
|
||||
filterset_fields = ("username", 'name')
|
||||
search_fields = ('username', 'name')
|
||||
serializer_classes = {
|
||||
'default': serializers.AccountTemplateSerializer
|
||||
|
||||
@@ -9,12 +9,12 @@
|
||||
name: "{{ account.username }}"
|
||||
password: "{{ account.secret | password_hash('des') }}"
|
||||
update_password: always
|
||||
when: account.secret_type == "password"
|
||||
when: secret_type == "password"
|
||||
|
||||
- name: create user If it already exists, no operation will be performed
|
||||
ansible.builtin.user:
|
||||
name: "{{ account.username }}"
|
||||
when: account.secret_type == "ssh_key"
|
||||
when: secret_type == "ssh_key"
|
||||
|
||||
- name: remove jumpserver ssh key
|
||||
ansible.builtin.lineinfile:
|
||||
@@ -22,7 +22,7 @@
|
||||
regexp: "{{ kwargs.regexp }}"
|
||||
state: absent
|
||||
when:
|
||||
- account.secret_type == "ssh_key"
|
||||
- secret_type == "ssh_key"
|
||||
- kwargs.strategy == "set_jms"
|
||||
|
||||
- name: Change SSH key
|
||||
@@ -30,7 +30,7 @@
|
||||
user: "{{ account.username }}"
|
||||
key: "{{ account.secret }}"
|
||||
exclusive: "{{ kwargs.exclusive }}"
|
||||
when: account.secret_type == "ssh_key"
|
||||
when: secret_type == "ssh_key"
|
||||
|
||||
- name: Refresh connection
|
||||
ansible.builtin.meta: reset_connection
|
||||
@@ -42,7 +42,7 @@
|
||||
ansible_user: "{{ account.username }}"
|
||||
ansible_password: "{{ account.secret }}"
|
||||
ansible_become: no
|
||||
when: account.secret_type == "password"
|
||||
when: secret_type == "password"
|
||||
|
||||
- name: Verify SSH key
|
||||
ansible.builtin.ping:
|
||||
@@ -51,4 +51,4 @@
|
||||
ansible_user: "{{ account.username }}"
|
||||
ansible_ssh_private_key_file: "{{ account.private_key_path }}"
|
||||
ansible_become: no
|
||||
when: account.secret_type == "ssh_key"
|
||||
when: secret_type == "ssh_key"
|
||||
|
||||
@@ -9,12 +9,12 @@
|
||||
name: "{{ account.username }}"
|
||||
password: "{{ account.secret | password_hash('sha512') }}"
|
||||
update_password: always
|
||||
when: account.secret_type == "password"
|
||||
when: secret_type == "password"
|
||||
|
||||
- name: create user If it already exists, no operation will be performed
|
||||
ansible.builtin.user:
|
||||
name: "{{ account.username }}"
|
||||
when: account.secret_type == "ssh_key"
|
||||
when: secret_type == "ssh_key"
|
||||
|
||||
- name: remove jumpserver ssh key
|
||||
ansible.builtin.lineinfile:
|
||||
@@ -22,7 +22,7 @@
|
||||
regexp: "{{ kwargs.regexp }}"
|
||||
state: absent
|
||||
when:
|
||||
- account.secret_type == "ssh_key"
|
||||
- secret_type == "ssh_key"
|
||||
- kwargs.strategy == "set_jms"
|
||||
|
||||
- name: Change SSH key
|
||||
@@ -30,7 +30,7 @@
|
||||
user: "{{ account.username }}"
|
||||
key: "{{ account.secret }}"
|
||||
exclusive: "{{ kwargs.exclusive }}"
|
||||
when: account.secret_type == "ssh_key"
|
||||
when: secret_type == "ssh_key"
|
||||
|
||||
- name: Refresh connection
|
||||
ansible.builtin.meta: reset_connection
|
||||
@@ -42,7 +42,7 @@
|
||||
ansible_user: "{{ account.username }}"
|
||||
ansible_password: "{{ account.secret }}"
|
||||
ansible_become: no
|
||||
when: account.secret_type == "password"
|
||||
when: secret_type == "password"
|
||||
|
||||
- name: Verify SSH key
|
||||
ansible.builtin.ping:
|
||||
@@ -51,4 +51,4 @@
|
||||
ansible_user: "{{ account.username }}"
|
||||
ansible_ssh_private_key_file: "{{ account.private_key_path }}"
|
||||
ansible_become: no
|
||||
when: account.secret_type == "ssh_key"
|
||||
when: secret_type == "ssh_key"
|
||||
|
||||
@@ -12,7 +12,7 @@ from accounts.models import ChangeSecretRecord
|
||||
from accounts.notifications import ChangeSecretExecutionTaskMsg
|
||||
from accounts.serializers import ChangeSecretRecordBackUpSerializer
|
||||
from assets.const import HostTypes
|
||||
from common.utils import get_logger
|
||||
from common.utils import get_logger, lazyproperty
|
||||
from common.utils.file import encrypt_and_compress_zip_file
|
||||
from common.utils.timezone import local_now_display
|
||||
from users.models import User
|
||||
@@ -28,23 +28,23 @@ class ChangeSecretManager(AccountBasePlaybookManager):
|
||||
def __init__(self, *args, **kwargs):
|
||||
super().__init__(*args, **kwargs)
|
||||
self.method_hosts_mapper = defaultdict(list)
|
||||
self.secret_type = self.execution.snapshot.get('secret_type')
|
||||
self.secret_type = self.execution.snapshot['secret_type']
|
||||
self.secret_strategy = self.execution.snapshot.get(
|
||||
'secret_strategy', SecretStrategy.custom
|
||||
)
|
||||
self.ssh_key_change_strategy = self.execution.snapshot.get(
|
||||
'ssh_key_change_strategy', SSHKeyStrategy.add
|
||||
)
|
||||
self.account_ids = self.execution.snapshot['accounts']
|
||||
self.snapshot_account_usernames = self.execution.snapshot['accounts']
|
||||
self.name_recorder_mapper = {} # 做个映射,方便后面处理
|
||||
|
||||
@classmethod
|
||||
def method_type(cls):
|
||||
return AutomationTypes.change_secret
|
||||
|
||||
def get_kwargs(self, account, secret, secret_type):
|
||||
def get_kwargs(self, account, secret):
|
||||
kwargs = {}
|
||||
if secret_type != SecretType.SSH_KEY:
|
||||
if self.secret_type != SecretType.SSH_KEY:
|
||||
return kwargs
|
||||
kwargs['strategy'] = self.ssh_key_change_strategy
|
||||
kwargs['exclusive'] = 'yes' if kwargs['strategy'] == SSHKeyStrategy.set else 'no'
|
||||
@@ -54,29 +54,18 @@ class ChangeSecretManager(AccountBasePlaybookManager):
|
||||
kwargs['regexp'] = '.*{}$'.format(secret.split()[2].strip())
|
||||
return kwargs
|
||||
|
||||
def secret_generator(self, secret_type):
|
||||
@lazyproperty
|
||||
def secret_generator(self):
|
||||
return SecretGenerator(
|
||||
self.secret_strategy, secret_type,
|
||||
self.secret_strategy, self.secret_type,
|
||||
self.execution.snapshot.get('password_rules')
|
||||
)
|
||||
|
||||
def get_secret(self, secret_type):
|
||||
def get_secret(self):
|
||||
if self.secret_strategy == SecretStrategy.custom:
|
||||
return self.execution.snapshot['secret']
|
||||
else:
|
||||
return self.secret_generator(secret_type).get_secret()
|
||||
|
||||
def get_accounts(self, privilege_account):
|
||||
if not privilege_account:
|
||||
print(f'not privilege account')
|
||||
return []
|
||||
|
||||
asset = privilege_account.asset
|
||||
accounts = asset.accounts.exclude(username=privilege_account.username)
|
||||
accounts = accounts.filter(id__in=self.account_ids)
|
||||
if self.secret_type:
|
||||
accounts = accounts.filter(secret_type=self.secret_type)
|
||||
return accounts
|
||||
return self.secret_generator.get_secret()
|
||||
|
||||
def host_callback(
|
||||
self, host, asset=None, account=None,
|
||||
@@ -89,10 +78,17 @@ class ChangeSecretManager(AccountBasePlaybookManager):
|
||||
if host.get('error'):
|
||||
return host
|
||||
|
||||
accounts = self.get_accounts(account)
|
||||
accounts = asset.accounts.all()
|
||||
if account:
|
||||
accounts = accounts.exclude(username=account.username)
|
||||
|
||||
if '*' not in self.snapshot_account_usernames:
|
||||
accounts = accounts.filter(username__in=self.snapshot_account_usernames)
|
||||
|
||||
accounts = accounts.filter(secret_type=self.secret_type)
|
||||
if not accounts:
|
||||
print('没有发现待改密账号: %s 用户ID: %s 类型: %s' % (
|
||||
asset.name, self.account_ids, self.secret_type
|
||||
print('没有发现待改密账号: %s 用户名: %s 类型: %s' % (
|
||||
asset.name, self.snapshot_account_usernames, self.secret_type
|
||||
))
|
||||
return []
|
||||
|
||||
@@ -101,16 +97,16 @@ class ChangeSecretManager(AccountBasePlaybookManager):
|
||||
method_hosts = [h for h in method_hosts if h != host['name']]
|
||||
inventory_hosts = []
|
||||
records = []
|
||||
host['secret_type'] = self.secret_type
|
||||
|
||||
if asset.type == HostTypes.WINDOWS and self.secret_type == SecretType.SSH_KEY:
|
||||
print(f'Windows {asset} does not support ssh key push')
|
||||
print(f'Windows {asset} does not support ssh key push \n')
|
||||
return inventory_hosts
|
||||
|
||||
for account in accounts:
|
||||
h = deepcopy(host)
|
||||
secret_type = account.secret_type
|
||||
h['name'] += '(' + account.username + ')'
|
||||
new_secret = self.get_secret(secret_type)
|
||||
new_secret = self.get_secret()
|
||||
|
||||
recorder = ChangeSecretRecord(
|
||||
asset=asset, account=account, execution=self.execution,
|
||||
@@ -120,15 +116,15 @@ class ChangeSecretManager(AccountBasePlaybookManager):
|
||||
self.name_recorder_mapper[h['name']] = recorder
|
||||
|
||||
private_key_path = None
|
||||
if secret_type == SecretType.SSH_KEY:
|
||||
if self.secret_type == SecretType.SSH_KEY:
|
||||
private_key_path = self.generate_private_key_path(new_secret, path_dir)
|
||||
new_secret = self.generate_public_key(new_secret)
|
||||
|
||||
h['kwargs'] = self.get_kwargs(account, new_secret, secret_type)
|
||||
h['kwargs'] = self.get_kwargs(account, new_secret)
|
||||
h['account'] = {
|
||||
'name': account.name,
|
||||
'username': account.username,
|
||||
'secret_type': secret_type,
|
||||
'secret_type': account.secret_type,
|
||||
'secret': new_secret,
|
||||
'private_key_path': private_key_path
|
||||
}
|
||||
|
||||
@@ -60,6 +60,4 @@ class GatherAccountsFilter:
|
||||
if not run_method_name:
|
||||
return info
|
||||
|
||||
if hasattr(self, f'{run_method_name}_filter'):
|
||||
return getattr(self, f'{run_method_name}_filter')(info)
|
||||
return info
|
||||
return getattr(self, f'{run_method_name}_filter')(info)
|
||||
|
||||
@@ -22,8 +22,8 @@ class GatherAccountsManager(AccountBasePlaybookManager):
|
||||
self.host_asset_mapper[host['name']] = asset
|
||||
return host
|
||||
|
||||
def filter_success_result(self, tp, result):
|
||||
result = GatherAccountsFilter(tp).run(self.method_id_meta_mapper, result)
|
||||
def filter_success_result(self, host, result):
|
||||
result = GatherAccountsFilter(host).run(self.method_id_meta_mapper, result)
|
||||
return result
|
||||
|
||||
@staticmethod
|
||||
|
||||
@@ -1,6 +1,9 @@
|
||||
from copy import deepcopy
|
||||
|
||||
from django.db.models import QuerySet
|
||||
|
||||
from accounts.const import AutomationTypes, SecretType
|
||||
from accounts.models import Account
|
||||
from assets.const import HostTypes
|
||||
from common.utils import get_logger
|
||||
from ..base.manager import AccountBasePlaybookManager
|
||||
@@ -16,6 +19,36 @@ class PushAccountManager(ChangeSecretManager, AccountBasePlaybookManager):
|
||||
def method_type(cls):
|
||||
return AutomationTypes.push_account
|
||||
|
||||
def create_nonlocal_accounts(self, accounts, snapshot_account_usernames, asset):
|
||||
secret_type = self.secret_type
|
||||
usernames = accounts.filter(secret_type=secret_type).values_list(
|
||||
'username', flat=True
|
||||
)
|
||||
create_usernames = set(snapshot_account_usernames) - set(usernames)
|
||||
create_account_objs = [
|
||||
Account(
|
||||
name=f'{username}-{secret_type}', username=username,
|
||||
secret_type=secret_type, asset=asset,
|
||||
)
|
||||
for username in create_usernames
|
||||
]
|
||||
Account.objects.bulk_create(create_account_objs)
|
||||
|
||||
def get_accounts(self, privilege_account, accounts: QuerySet):
|
||||
if not privilege_account:
|
||||
print(f'not privilege account')
|
||||
return []
|
||||
snapshot_account_usernames = self.execution.snapshot['accounts']
|
||||
if '*' in snapshot_account_usernames:
|
||||
return accounts.exclude(username=privilege_account.username)
|
||||
|
||||
asset = privilege_account.asset
|
||||
self.create_nonlocal_accounts(accounts, snapshot_account_usernames, asset)
|
||||
accounts = asset.accounts.exclude(username=privilege_account.username).filter(
|
||||
username__in=snapshot_account_usernames, secret_type=self.secret_type
|
||||
)
|
||||
return accounts
|
||||
|
||||
def host_callback(self, host, asset=None, account=None, automation=None, path_dir=None, **kwargs):
|
||||
host = super(ChangeSecretManager, self).host_callback(
|
||||
host, asset=asset, account=account, automation=automation,
|
||||
@@ -24,36 +57,34 @@ class PushAccountManager(ChangeSecretManager, AccountBasePlaybookManager):
|
||||
if host.get('error'):
|
||||
return host
|
||||
|
||||
accounts = self.get_accounts(account)
|
||||
accounts = asset.accounts.all()
|
||||
accounts = self.get_accounts(account, accounts)
|
||||
inventory_hosts = []
|
||||
host['secret_type'] = self.secret_type
|
||||
if asset.type == HostTypes.WINDOWS and self.secret_type == SecretType.SSH_KEY:
|
||||
msg = f'Windows {asset} does not support ssh key push'
|
||||
msg = f'Windows {asset} does not support ssh key push \n'
|
||||
print(msg)
|
||||
return inventory_hosts
|
||||
|
||||
for account in accounts:
|
||||
h = deepcopy(host)
|
||||
secret_type = account.secret_type
|
||||
h['name'] += '(' + account.username + ')'
|
||||
if self.secret_type is None:
|
||||
new_secret = account.secret
|
||||
else:
|
||||
new_secret = self.get_secret(secret_type)
|
||||
new_secret = self.get_secret()
|
||||
|
||||
self.name_recorder_mapper[h['name']] = {
|
||||
'account': account, 'new_secret': new_secret,
|
||||
}
|
||||
|
||||
private_key_path = None
|
||||
if secret_type == SecretType.SSH_KEY:
|
||||
if self.secret_type == SecretType.SSH_KEY:
|
||||
private_key_path = self.generate_private_key_path(new_secret, path_dir)
|
||||
new_secret = self.generate_public_key(new_secret)
|
||||
|
||||
h['kwargs'] = self.get_kwargs(account, new_secret, secret_type)
|
||||
h['kwargs'] = self.get_kwargs(account, new_secret)
|
||||
h['account'] = {
|
||||
'name': account.name,
|
||||
'username': account.username,
|
||||
'secret_type': secret_type,
|
||||
'secret_type': account.secret_type,
|
||||
'secret': new_secret,
|
||||
'private_key_path': private_key_path
|
||||
}
|
||||
@@ -81,9 +112,9 @@ class PushAccountManager(ChangeSecretManager, AccountBasePlaybookManager):
|
||||
logger.error("Pust account error: ", e)
|
||||
|
||||
def run(self, *args, **kwargs):
|
||||
if self.secret_type and not self.check_secret():
|
||||
if not self.check_secret():
|
||||
return
|
||||
super(ChangeSecretManager, self).run(*args, **kwargs)
|
||||
super().run(*args, **kwargs)
|
||||
|
||||
# @classmethod
|
||||
# def trigger_by_asset_create(cls, asset):
|
||||
|
||||
@@ -25,15 +25,6 @@ class VerifyAccountManager(AccountBasePlaybookManager):
|
||||
f.write('ssh_args = -o ControlMaster=no -o ControlPersist=no\n')
|
||||
return path
|
||||
|
||||
@classmethod
|
||||
def method_type(cls):
|
||||
return AutomationTypes.verify_account
|
||||
|
||||
def get_accounts(self, privilege_account, accounts: QuerySet):
|
||||
account_ids = self.execution.snapshot['accounts']
|
||||
accounts = accounts.filter(id__in=account_ids)
|
||||
return accounts
|
||||
|
||||
def host_callback(self, host, asset=None, account=None, automation=None, path_dir=None, **kwargs):
|
||||
host = super().host_callback(
|
||||
host, asset=asset, account=account,
|
||||
@@ -71,6 +62,16 @@ class VerifyAccountManager(AccountBasePlaybookManager):
|
||||
inventory_hosts.append(h)
|
||||
return inventory_hosts
|
||||
|
||||
@classmethod
|
||||
def method_type(cls):
|
||||
return AutomationTypes.verify_account
|
||||
|
||||
def get_accounts(self, privilege_account, accounts: QuerySet):
|
||||
snapshot_account_usernames = self.execution.snapshot['accounts']
|
||||
if '*' not in snapshot_account_usernames:
|
||||
accounts = accounts.filter(username__in=snapshot_account_usernames)
|
||||
return accounts
|
||||
|
||||
def on_host_success(self, host, result):
|
||||
account = self.host_account_mapper.get(host)
|
||||
account.set_connectivity(Connectivity.OK)
|
||||
|
||||
@@ -1,6 +1,6 @@
|
||||
from common.utils import get_logger
|
||||
from accounts.const import AutomationTypes
|
||||
from assets.automations.ping_gateway.manager import PingGatewayManager
|
||||
from common.utils import get_logger
|
||||
|
||||
logger = get_logger(__name__)
|
||||
|
||||
@@ -16,6 +16,6 @@ class VerifyGatewayAccountManager(PingGatewayManager):
|
||||
logger.info(">>> 开始执行测试网关账号可连接性任务")
|
||||
|
||||
def get_accounts(self, gateway):
|
||||
account_ids = self.execution.snapshot['accounts']
|
||||
accounts = gateway.accounts.filter(id__in=account_ids)
|
||||
usernames = self.execution.snapshot['accounts']
|
||||
accounts = gateway.accounts.filter(username__in=usernames)
|
||||
return accounts
|
||||
|
||||
@@ -1,69 +0,0 @@
|
||||
# Generated by Django 3.2.16 on 2023-03-07 07:36
|
||||
|
||||
from django.db import migrations
|
||||
from django.db.models import Q
|
||||
|
||||
|
||||
def get_nodes_all_assets(apps, *nodes):
|
||||
node_model = apps.get_model('assets', 'Node')
|
||||
asset_model = apps.get_model('assets', 'Asset')
|
||||
node_ids = set()
|
||||
descendant_node_query = Q()
|
||||
for n in nodes:
|
||||
node_ids.add(n.id)
|
||||
descendant_node_query |= Q(key__istartswith=f'{n.key}:')
|
||||
if descendant_node_query:
|
||||
_ids = node_model.objects.order_by().filter(descendant_node_query).values_list('id', flat=True)
|
||||
node_ids.update(_ids)
|
||||
return asset_model.objects.order_by().filter(nodes__id__in=node_ids).distinct()
|
||||
|
||||
|
||||
def get_all_assets(apps, snapshot):
|
||||
node_model = apps.get_model('assets', 'Node')
|
||||
asset_model = apps.get_model('assets', 'Asset')
|
||||
asset_ids = snapshot.get('assets', [])
|
||||
node_ids = snapshot.get('nodes', [])
|
||||
|
||||
nodes = node_model.objects.filter(id__in=node_ids)
|
||||
node_asset_ids = get_nodes_all_assets(apps, *nodes).values_list('id', flat=True)
|
||||
asset_ids = set(list(asset_ids) + list(node_asset_ids))
|
||||
return asset_model.objects.filter(id__in=asset_ids)
|
||||
|
||||
|
||||
def migrate_account_usernames_to_ids(apps, schema_editor):
|
||||
db_alias = schema_editor.connection.alias
|
||||
execution_model = apps.get_model('accounts', 'AutomationExecution')
|
||||
account_model = apps.get_model('accounts', 'Account')
|
||||
executions = execution_model.objects.using(db_alias).all()
|
||||
executions_update = []
|
||||
for execution in executions:
|
||||
snapshot = execution.snapshot
|
||||
accounts = account_model.objects.none()
|
||||
account_usernames = snapshot.get('accounts', [])
|
||||
for asset in get_all_assets(apps, snapshot):
|
||||
accounts = accounts | asset.accounts.all()
|
||||
secret_type = snapshot.get('secret_type')
|
||||
if secret_type:
|
||||
ids = accounts.filter(
|
||||
username__in=account_usernames,
|
||||
secret_type=secret_type
|
||||
).values_list('id', flat=True)
|
||||
else:
|
||||
ids = accounts.filter(
|
||||
username__in=account_usernames
|
||||
).values_list('id', flat=True)
|
||||
snapshot['accounts'] = [str(_id) for _id in ids]
|
||||
execution.snapshot = snapshot
|
||||
executions_update.append(execution)
|
||||
|
||||
execution_model.objects.bulk_update(executions_update, ['snapshot'])
|
||||
|
||||
|
||||
class Migration(migrations.Migration):
|
||||
dependencies = [
|
||||
('accounts', '0008_alter_gatheredaccount_options'),
|
||||
]
|
||||
|
||||
operations = [
|
||||
migrations.RunPython(migrate_account_usernames_to_ids),
|
||||
]
|
||||
@@ -1,12 +1,11 @@
|
||||
from django.db import models
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
|
||||
from common.db import fields
|
||||
from common.db.models import JMSBaseModel
|
||||
from accounts.const import (
|
||||
AutomationTypes, SecretType, SecretStrategy, SSHKeyStrategy
|
||||
)
|
||||
from accounts.models import Account
|
||||
from common.db import fields
|
||||
from common.db.models import JMSBaseModel
|
||||
from .base import AccountBaseAutomation
|
||||
|
||||
__all__ = ['ChangeSecretAutomation', 'ChangeSecretRecord', 'ChangeSecretMixin']
|
||||
@@ -28,35 +27,18 @@ class ChangeSecretMixin(models.Model):
|
||||
default=SSHKeyStrategy.add, verbose_name=_('SSH key change strategy')
|
||||
)
|
||||
|
||||
accounts: list[str] # account usernames
|
||||
get_all_assets: callable # get all assets
|
||||
|
||||
class Meta:
|
||||
abstract = True
|
||||
|
||||
def create_nonlocal_accounts(self, usernames, asset):
|
||||
pass
|
||||
|
||||
def get_account_ids(self):
|
||||
usernames = self.accounts
|
||||
accounts = Account.objects.none()
|
||||
for asset in self.get_all_assets():
|
||||
self.create_nonlocal_accounts(usernames, asset)
|
||||
accounts = accounts | asset.accounts.all()
|
||||
account_ids = accounts.filter(
|
||||
username__in=usernames, secret_type=self.secret_type
|
||||
).values_list('id', flat=True)
|
||||
return [str(_id) for _id in account_ids]
|
||||
|
||||
def to_attr_json(self):
|
||||
attr_json = super().to_attr_json()
|
||||
attr_json.update({
|
||||
'secret': self.secret,
|
||||
'secret_type': self.secret_type,
|
||||
'accounts': self.get_account_ids(),
|
||||
'password_rules': self.password_rules,
|
||||
'secret_strategy': self.secret_strategy,
|
||||
'password_rules': self.password_rules,
|
||||
'ssh_key_change_strategy': self.ssh_key_change_strategy,
|
||||
|
||||
})
|
||||
return attr_json
|
||||
|
||||
|
||||
@@ -2,8 +2,6 @@ from django.db import models
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
|
||||
from accounts.const import AutomationTypes
|
||||
from accounts.models import Account
|
||||
from jumpserver.utils import has_valid_xpack_license
|
||||
from .base import AccountBaseAutomation
|
||||
from .change_secret import ChangeSecretMixin
|
||||
|
||||
@@ -15,21 +13,6 @@ class PushAccountAutomation(ChangeSecretMixin, AccountBaseAutomation):
|
||||
username = models.CharField(max_length=128, verbose_name=_('Username'))
|
||||
action = models.CharField(max_length=16, verbose_name=_('Action'))
|
||||
|
||||
def create_nonlocal_accounts(self, usernames, asset):
|
||||
secret_type = self.secret_type
|
||||
account_usernames = asset.accounts.filter(secret_type=self.secret_type).values_list(
|
||||
'username', flat=True
|
||||
)
|
||||
create_usernames = set(usernames) - set(account_usernames)
|
||||
create_account_objs = [
|
||||
Account(
|
||||
name=f'{username}-{secret_type}', username=username,
|
||||
secret_type=secret_type, asset=asset,
|
||||
)
|
||||
for username in create_usernames
|
||||
]
|
||||
Account.objects.bulk_create(create_account_objs)
|
||||
|
||||
def set_period_schedule(self):
|
||||
pass
|
||||
|
||||
@@ -44,8 +27,6 @@ class PushAccountAutomation(ChangeSecretMixin, AccountBaseAutomation):
|
||||
|
||||
def save(self, *args, **kwargs):
|
||||
self.type = AutomationTypes.push_account
|
||||
if not has_valid_xpack_license():
|
||||
self.is_periodic = False
|
||||
super().save(*args, **kwargs)
|
||||
|
||||
def to_attr_json(self):
|
||||
|
||||
@@ -12,7 +12,7 @@ from accounts.const import SecretType
|
||||
from common.db import fields
|
||||
from common.utils import (
|
||||
ssh_key_string_to_obj, ssh_key_gen, get_logger,
|
||||
random_string, lazyproperty, parse_ssh_public_key_str, is_openssh_format_key
|
||||
random_string, lazyproperty, parse_ssh_public_key_str
|
||||
)
|
||||
from orgs.mixins.models import JMSOrgBaseModel, OrgManager
|
||||
|
||||
@@ -118,13 +118,7 @@ class BaseAccount(JMSOrgBaseModel):
|
||||
key_name = '.' + md5(self.private_key.encode('utf-8')).hexdigest()
|
||||
key_path = os.path.join(tmp_dir, key_name)
|
||||
if not os.path.exists(key_path):
|
||||
# https://github.com/ansible/ansible-runner/issues/544
|
||||
# ssh requires OpenSSH format keys to have a full ending newline.
|
||||
# It does not require this for old-style PEM keys.
|
||||
with open(key_path, 'w') as f:
|
||||
f.write(self.secret)
|
||||
if is_openssh_format_key(self.secret.encode('utf-8')):
|
||||
f.write("\n")
|
||||
self.private_key_obj.write_private_key_file(key_path)
|
||||
os.chmod(key_path, 0o400)
|
||||
return key_path
|
||||
|
||||
|
||||
@@ -81,7 +81,7 @@ class AccountAssetSerializer(serializers.ModelSerializer):
|
||||
|
||||
def to_internal_value(self, data):
|
||||
if isinstance(data, dict):
|
||||
i = data.get('id') or data.get('pk')
|
||||
i = data.get('id')
|
||||
else:
|
||||
i = data
|
||||
|
||||
@@ -135,15 +135,8 @@ class AccountHistorySerializer(serializers.ModelSerializer):
|
||||
|
||||
class Meta:
|
||||
model = Account.history.model
|
||||
fields = [
|
||||
'id', 'secret', 'secret_type', 'version', 'history_date',
|
||||
'history_user'
|
||||
]
|
||||
fields = ['id', 'secret', 'secret_type', 'version', 'history_date', 'history_user']
|
||||
read_only_fields = fields
|
||||
extra_kwargs = {
|
||||
'history_user': {'label': _('User')},
|
||||
'history_date': {'label': _('Date')},
|
||||
}
|
||||
|
||||
|
||||
class AccountTaskSerializer(serializers.Serializer):
|
||||
|
||||
@@ -33,8 +33,7 @@ class AuthValidateMixin(serializers.Serializer):
|
||||
return secret
|
||||
elif secret_type == SecretType.SSH_KEY:
|
||||
passphrase = passphrase if passphrase else None
|
||||
secret = validate_ssh_key(secret, passphrase)
|
||||
return secret
|
||||
return validate_ssh_key(secret, passphrase)
|
||||
else:
|
||||
return secret
|
||||
|
||||
@@ -42,9 +41,8 @@ class AuthValidateMixin(serializers.Serializer):
|
||||
secret_type = validated_data.get('secret_type')
|
||||
passphrase = validated_data.get('passphrase')
|
||||
secret = validated_data.pop('secret', None)
|
||||
validated_data['secret'] = self.handle_secret(
|
||||
secret, secret_type, passphrase
|
||||
)
|
||||
self.handle_secret(secret, secret_type, passphrase)
|
||||
validated_data['secret'] = secret
|
||||
for field in ('secret',):
|
||||
value = validated_data.get(field)
|
||||
if not value:
|
||||
|
||||
@@ -23,10 +23,12 @@ def push_accounts_to_assets_task(account_ids):
|
||||
task_name = gettext_noop("Push accounts to assets")
|
||||
task_name = PushAccountAutomation.generate_unique_name(task_name)
|
||||
|
||||
task_snapshot = {
|
||||
'accounts': [str(account.id) for account in accounts],
|
||||
'assets': [str(account.asset_id) for account in accounts],
|
||||
}
|
||||
|
||||
tp = AutomationTypes.push_account
|
||||
quickstart_automation_by_snapshot(task_name, tp, task_snapshot)
|
||||
for account in accounts:
|
||||
task_snapshot = {
|
||||
'secret': account.secret,
|
||||
'secret_type': account.secret_type,
|
||||
'accounts': [account.username],
|
||||
'assets': [str(account.asset_id)],
|
||||
}
|
||||
tp = AutomationTypes.push_account
|
||||
quickstart_automation_by_snapshot(task_name, tp, task_snapshot)
|
||||
|
||||
@@ -17,9 +17,9 @@ __all__ = [
|
||||
def verify_connectivity_util(assets, tp, accounts, task_name):
|
||||
if not assets or not accounts:
|
||||
return
|
||||
account_ids = [str(account.id) for account in accounts]
|
||||
account_usernames = list(accounts.values_list('username', flat=True))
|
||||
task_snapshot = {
|
||||
'accounts': account_ids,
|
||||
'accounts': account_usernames,
|
||||
'assets': [str(asset.id) for asset in assets],
|
||||
}
|
||||
quickstart_automation_by_snapshot(task_name, tp, task_snapshot)
|
||||
|
||||
@@ -12,7 +12,8 @@ from django.utils.translation import gettext as _
|
||||
from sshtunnel import SSHTunnelForwarder, BaseSSHTunnelForwarderError
|
||||
|
||||
from assets.automations.methods import platform_automation_methods
|
||||
from common.utils import get_logger, lazyproperty, is_openssh_format_key, ssh_pubkey_gen
|
||||
from common.utils import get_logger, lazyproperty
|
||||
from common.utils import ssh_pubkey_gen, ssh_key_string_to_obj
|
||||
from ops.ansible import JMSInventory, PlaybookRunner, DefaultCallback
|
||||
|
||||
logger = get_logger(__name__)
|
||||
@@ -126,13 +127,7 @@ class BasePlaybookManager:
|
||||
key_path = os.path.join(path_dir, key_name)
|
||||
|
||||
if not os.path.exists(key_path):
|
||||
# https://github.com/ansible/ansible-runner/issues/544
|
||||
# ssh requires OpenSSH format keys to have a full ending newline.
|
||||
# It does not require this for old-style PEM keys.
|
||||
with open(key_path, 'w') as f:
|
||||
f.write(secret)
|
||||
if is_openssh_format_key(secret.encode('utf-8')):
|
||||
f.write("\n")
|
||||
ssh_key_string_to_obj(secret, password=None).write_private_key_file(key_path)
|
||||
os.chmod(key_path, 0o400)
|
||||
return key_path
|
||||
|
||||
|
||||
@@ -1,35 +0,0 @@
|
||||
__all__ = ['FormatAssetInfo']
|
||||
|
||||
|
||||
class FormatAssetInfo:
|
||||
|
||||
def __init__(self, tp):
|
||||
self.tp = tp
|
||||
|
||||
@staticmethod
|
||||
def posix_format(info):
|
||||
for cpu_model in info.get('cpu_model', []):
|
||||
if cpu_model.endswith('GHz') or cpu_model.startswith("Intel"):
|
||||
break
|
||||
else:
|
||||
cpu_model = ''
|
||||
info['cpu_model'] = cpu_model[:48]
|
||||
info['cpu_count'] = info.get('cpu_count', 0)
|
||||
return info
|
||||
|
||||
def run(self, method_id_meta_mapper, info):
|
||||
for k, v in info.items():
|
||||
info[k] = v.strip() if isinstance(v, str) else v
|
||||
|
||||
run_method_name = None
|
||||
for k, v in method_id_meta_mapper.items():
|
||||
if self.tp not in v['type']:
|
||||
continue
|
||||
run_method_name = k.replace(f'{v["method"]}_', '')
|
||||
|
||||
if not run_method_name:
|
||||
return info
|
||||
|
||||
if hasattr(self, f'{run_method_name}_format'):
|
||||
return getattr(self, f'{run_method_name}_format')(info)
|
||||
return info
|
||||
@@ -11,7 +11,7 @@
|
||||
cpu_count: "{{ ansible_processor_count }}"
|
||||
cpu_cores: "{{ ansible_processor_cores }}"
|
||||
cpu_vcpus: "{{ ansible_processor_vcpus }}"
|
||||
memory: "{{ ansible_memtotal_mb / 1024 | round(2) }}"
|
||||
memory: "{{ ansible_memtotal_mb }}"
|
||||
disk_total: "{{ (ansible_mounts | map(attribute='size_total') | sum / 1024 / 1024 / 1024) | round(2) }}"
|
||||
distribution: "{{ ansible_distribution }}"
|
||||
distribution_version: "{{ ansible_distribution_version }}"
|
||||
|
||||
@@ -1,6 +1,5 @@
|
||||
from assets.const import AutomationTypes
|
||||
from common.utils import get_logger
|
||||
from .format_asset_info import FormatAssetInfo
|
||||
from assets.const import AutomationTypes
|
||||
from ..base.manager import BasePlaybookManager
|
||||
|
||||
logger = get_logger(__name__)
|
||||
@@ -20,16 +19,13 @@ class GatherFactsManager(BasePlaybookManager):
|
||||
self.host_asset_mapper[host['name']] = asset
|
||||
return host
|
||||
|
||||
def format_asset_info(self, tp, info):
|
||||
info = FormatAssetInfo(tp).run(self.method_id_meta_mapper, info)
|
||||
return info
|
||||
|
||||
def on_host_success(self, host, result):
|
||||
info = result.get('debug', {}).get('res', {}).get('info', {})
|
||||
asset = self.host_asset_mapper.get(host)
|
||||
if asset and info:
|
||||
info = self.format_asset_info(asset.type, info)
|
||||
for k, v in info.items():
|
||||
info[k] = v.strip() if isinstance(v, str) else v
|
||||
asset.info = info
|
||||
asset.save(update_fields=['info'])
|
||||
asset.save()
|
||||
else:
|
||||
logger.error("Not found info: {}".format(host))
|
||||
|
||||
@@ -1,12 +1,10 @@
|
||||
from django.utils.translation import gettext_lazy as _
|
||||
|
||||
from .base import BaseType
|
||||
|
||||
|
||||
class CloudTypes(BaseType):
|
||||
PUBLIC = 'public', _('Public cloud')
|
||||
PRIVATE = 'private', _('Private cloud')
|
||||
K8S = 'k8s', _('Kubernetes')
|
||||
PUBLIC = 'public', 'Public cloud'
|
||||
PRIVATE = 'private', 'Private cloud'
|
||||
K8S = 'k8s', 'Kubernetes'
|
||||
|
||||
@classmethod
|
||||
def _get_base_constrains(cls) -> dict:
|
||||
|
||||
@@ -1,5 +1,3 @@
|
||||
from django.utils.translation import gettext_lazy as _
|
||||
|
||||
from .base import BaseType
|
||||
|
||||
GATEWAY_NAME = 'Gateway'
|
||||
@@ -9,7 +7,7 @@ class HostTypes(BaseType):
|
||||
LINUX = 'linux', 'Linux'
|
||||
WINDOWS = 'windows', 'Windows'
|
||||
UNIX = 'unix', 'Unix'
|
||||
OTHER_HOST = 'other', _("Other")
|
||||
OTHER_HOST = 'other', "Other"
|
||||
|
||||
@classmethod
|
||||
def _get_base_constrains(cls) -> dict:
|
||||
|
||||
@@ -39,7 +39,7 @@ class Protocol(ChoicesMixin, models.TextChoices):
|
||||
'port': 3389,
|
||||
'secret_types': ['password'],
|
||||
'setting': {
|
||||
'console': False,
|
||||
'console': True,
|
||||
'security': 'any',
|
||||
}
|
||||
},
|
||||
|
||||
@@ -214,13 +214,10 @@ class AllTypes(ChoicesMixin):
|
||||
tp_node = cls.choice_to_node(tp, category_node['id'], opened=False, meta=meta)
|
||||
tp_count = category_type_mapper.get(category + '_' + tp, 0)
|
||||
tp_node['name'] += f'({tp_count})'
|
||||
platforms = tp_platforms.get(category + '_' + tp, [])
|
||||
if not platforms:
|
||||
tp_node['isParent'] = False
|
||||
nodes.append(tp_node)
|
||||
|
||||
# Platform 格式化
|
||||
for p in platforms:
|
||||
for p in tp_platforms.get(category + '_' + tp, []):
|
||||
platform_node = cls.platform_to_node(p, tp_node['id'], include_asset)
|
||||
platform_node['name'] += f'({platform_count.get(p.id, 0)})'
|
||||
nodes.append(platform_node)
|
||||
@@ -309,11 +306,10 @@ class AllTypes(ChoicesMixin):
|
||||
protocols_data = deepcopy(default_protocols)
|
||||
if _protocols:
|
||||
protocols_data = [p for p in protocols_data if p['name'] in _protocols]
|
||||
|
||||
for p in protocols_data:
|
||||
setting = _protocols_setting.get(p['name'], {})
|
||||
p['required'] = setting.pop('required', False)
|
||||
p['default'] = setting.pop('default', False)
|
||||
p['required'] = p.pop('required', False)
|
||||
p['default'] = p.pop('default', False)
|
||||
p['setting'] = {**p.get('setting', {}), **setting}
|
||||
|
||||
platform_data = {
|
||||
|
||||
@@ -34,9 +34,8 @@ def migrate_database_to_asset(apps, *args):
|
||||
_attrs = app.attrs or {}
|
||||
attrs.update(_attrs)
|
||||
|
||||
name = 'DB-{}'.format(app.name)
|
||||
db = db_model(
|
||||
id=app.id, name=name, address=attrs['host'],
|
||||
id=app.id, name=app.name, address=attrs['host'],
|
||||
protocols='{}/{}'.format(app.type, attrs['port']),
|
||||
db_name=attrs['database'] or '',
|
||||
platform=platforms_map[app.type],
|
||||
@@ -62,9 +61,8 @@ def migrate_cloud_to_asset(apps, *args):
|
||||
for app in applications:
|
||||
attrs = app.attrs
|
||||
print("\t- Create cloud: {}".format(app.name))
|
||||
name = 'Cloud-{}'.format(app.name)
|
||||
cloud = cloud_model(
|
||||
id=app.id, name=name,
|
||||
id=app.id, name=app.name,
|
||||
address=attrs.get('cluster', ''),
|
||||
protocols='k8s/443', platform=platform,
|
||||
org_id=app.org_id,
|
||||
|
||||
@@ -1,29 +0,0 @@
|
||||
# Generated by Django 3.2.17 on 2023-03-15 09:41
|
||||
|
||||
from django.db import migrations
|
||||
|
||||
|
||||
def set_windows_platform_non_console(apps, schema_editor):
|
||||
Platform = apps.get_model('assets', 'Platform')
|
||||
names = ['Windows', 'Windows-RDP', 'Windows-TLS', 'RemoteAppHost']
|
||||
windows = Platform.objects.filter(name__in=names)
|
||||
if not windows:
|
||||
return
|
||||
|
||||
for p in windows:
|
||||
rdp = p.protocols.filter(name='rdp').first()
|
||||
if not rdp:
|
||||
continue
|
||||
rdp.setting['console'] = False
|
||||
rdp.save()
|
||||
|
||||
|
||||
class Migration(migrations.Migration):
|
||||
|
||||
dependencies = [
|
||||
('assets', '0109_alter_asset_options'),
|
||||
]
|
||||
|
||||
operations = [
|
||||
migrations.RunPython(set_windows_platform_non_console)
|
||||
]
|
||||
@@ -108,7 +108,7 @@ class Asset(NodesRelationMixin, AbsConnectivity, JMSOrgBaseModel):
|
||||
verbose_name=_("Nodes"))
|
||||
is_active = models.BooleanField(default=True, verbose_name=_('Is active'))
|
||||
labels = models.ManyToManyField('assets.Label', blank=True, related_name='assets', verbose_name=_("Labels"))
|
||||
info = models.JSONField(verbose_name=_('Info'), default=dict, blank=True) # 资产的一些信息,如 硬件信息
|
||||
info = models.JSONField(verbose_name='Info', default=dict, blank=True) # 资产的一些信息,如 硬件信息
|
||||
|
||||
objects = AssetManager.from_queryset(AssetQuerySet)()
|
||||
|
||||
|
||||
@@ -11,7 +11,7 @@ __all__ = ['Platform', 'PlatformProtocol', 'PlatformAutomation']
|
||||
|
||||
class PlatformProtocol(models.Model):
|
||||
SETTING_ATTRS = {
|
||||
'console': False,
|
||||
'console': True,
|
||||
'security': 'any,tls,rdp',
|
||||
'sftp_enabled': True,
|
||||
'sftp_home': '/tmp'
|
||||
|
||||
@@ -26,13 +26,6 @@ __all__ = [
|
||||
class AssetProtocolsSerializer(serializers.ModelSerializer):
|
||||
port = serializers.IntegerField(required=False, allow_null=True, max_value=65535, min_value=1)
|
||||
|
||||
def to_file_representation(self, data):
|
||||
return '{name}/{port}'.format(**data)
|
||||
|
||||
def to_file_internal_value(self, data):
|
||||
name, port = data.split('/')
|
||||
return {'name': name, 'port': port}
|
||||
|
||||
class Meta:
|
||||
model = Protocol
|
||||
fields = ['name', 'port']
|
||||
@@ -71,8 +64,7 @@ class AssetAccountSerializer(
|
||||
template = serializers.BooleanField(
|
||||
default=False, label=_("Template"), write_only=True
|
||||
)
|
||||
name = serializers.CharField(max_length=128, required=False, label=_("Name"))
|
||||
secret_type = serializers.CharField(max_length=64, default='password', label=_("Secret type"))
|
||||
name = serializers.CharField(max_length=128, required=True, label=_("Name"))
|
||||
|
||||
class Meta:
|
||||
model = Account
|
||||
@@ -81,7 +73,7 @@ class AssetAccountSerializer(
|
||||
'is_active', 'version', 'secret_type',
|
||||
]
|
||||
fields_write_only = [
|
||||
'secret', 'passphrase', 'push_now', 'template'
|
||||
'secret', 'push_now', 'template'
|
||||
]
|
||||
fields = fields_mini + fields_write_only
|
||||
extra_kwargs = {
|
||||
@@ -129,8 +121,7 @@ class AssetSerializer(BulkOrgResourceModelSerializer, WritableNestedModelSeriali
|
||||
type = LabeledChoiceField(choices=AllTypes.choices(), read_only=True, label=_('Type'))
|
||||
labels = AssetLabelSerializer(many=True, required=False, label=_('Label'))
|
||||
protocols = AssetProtocolsSerializer(many=True, required=False, label=_('Protocols'), default=())
|
||||
accounts = AssetAccountSerializer(many=True, required=False, allow_null=True, write_only=True, label=_('Account'))
|
||||
nodes_display = serializers.ListField(read_only=True, label=_("Node path"))
|
||||
accounts = AssetAccountSerializer(many=True, required=False, write_only=True, label=_('Account'))
|
||||
|
||||
class Meta:
|
||||
model = Asset
|
||||
@@ -142,11 +133,11 @@ class AssetSerializer(BulkOrgResourceModelSerializer, WritableNestedModelSeriali
|
||||
'nodes_display', 'accounts'
|
||||
]
|
||||
read_only_fields = [
|
||||
'category', 'type', 'connectivity', 'auto_info',
|
||||
'category', 'type', 'connectivity',
|
||||
'date_verified', 'created_by', 'date_created',
|
||||
'auto_info',
|
||||
]
|
||||
fields = fields_small + fields_fk + fields_m2m + read_only_fields
|
||||
fields_unexport = ['auto_info']
|
||||
extra_kwargs = {
|
||||
'auto_info': {'label': _('Auto info')},
|
||||
'name': {'label': _("Name")},
|
||||
@@ -159,7 +150,7 @@ class AssetSerializer(BulkOrgResourceModelSerializer, WritableNestedModelSeriali
|
||||
self._init_field_choices()
|
||||
|
||||
def _get_protocols_required_default(self):
|
||||
platform = self._asset_platform
|
||||
platform = self._initial_data_platform
|
||||
platform_protocols = platform.protocols.all()
|
||||
protocols_default = [p for p in platform_protocols if p.default]
|
||||
protocols_required = [p for p in platform_protocols if p.required or p.primary]
|
||||
@@ -215,22 +206,20 @@ class AssetSerializer(BulkOrgResourceModelSerializer, WritableNestedModelSeriali
|
||||
instance.nodes.set(nodes_to_set)
|
||||
|
||||
@property
|
||||
def _asset_platform(self):
|
||||
def _initial_data_platform(self):
|
||||
if self.instance:
|
||||
return self.instance.platform
|
||||
|
||||
platform_id = self.initial_data.get('platform')
|
||||
if isinstance(platform_id, dict):
|
||||
platform_id = platform_id.get('id') or platform_id.get('pk')
|
||||
|
||||
if not platform_id and self.instance:
|
||||
platform = self.instance.platform
|
||||
else:
|
||||
platform = Platform.objects.filter(id=platform_id).first()
|
||||
|
||||
platform = Platform.objects.filter(id=platform_id).first()
|
||||
if not platform:
|
||||
raise serializers.ValidationError({'platform': _("Platform not exist")})
|
||||
return platform
|
||||
|
||||
def validate_domain(self, value):
|
||||
platform = self._asset_platform
|
||||
platform = self._initial_data_platform
|
||||
if platform.domain_enabled:
|
||||
return value
|
||||
else:
|
||||
@@ -274,8 +263,6 @@ class AssetSerializer(BulkOrgResourceModelSerializer, WritableNestedModelSeriali
|
||||
|
||||
@staticmethod
|
||||
def accounts_create(accounts_data, asset):
|
||||
if not accounts_data:
|
||||
return
|
||||
for data in accounts_data:
|
||||
data['asset'] = asset
|
||||
AssetAccountSerializer().create(data)
|
||||
|
||||
@@ -1,25 +1,26 @@
|
||||
from django.utils.translation import gettext_lazy as _
|
||||
from rest_framework import serializers
|
||||
from django.utils.translation import gettext_lazy as _
|
||||
|
||||
from assets.models import Host
|
||||
from .common import AssetSerializer
|
||||
|
||||
|
||||
__all__ = ['HostInfoSerializer', 'HostSerializer']
|
||||
|
||||
|
||||
class HostInfoSerializer(serializers.Serializer):
|
||||
vendor = serializers.CharField(max_length=64, required=False, allow_blank=True, label=_('Vendor'))
|
||||
model = serializers.CharField(max_length=54, required=False, allow_blank=True, label=_('Model'))
|
||||
sn = serializers.CharField(max_length=128, required=False, allow_blank=True, label=_('Serial number'))
|
||||
cpu_model = serializers.CharField(max_length=64, allow_blank=True, required=False, label=_('CPU model'))
|
||||
cpu_count = serializers.CharField(max_length=64, required=False, allow_blank=True, label=_('CPU count'))
|
||||
cpu_cores = serializers.CharField(max_length=64, required=False, allow_blank=True, label=_('CPU cores'))
|
||||
cpu_vcpus = serializers.CharField(max_length=64, required=False, allow_blank=True, label=_('CPU vcpus'))
|
||||
model = serializers.CharField(max_length=54, required=False, allow_blank=True, label=_('Model'))
|
||||
sn = serializers.CharField(max_length=128, required=False, allow_blank=True, label=_('Serial number'))
|
||||
cpu_model = serializers.ListField(child=serializers.CharField(max_length=64, allow_blank=True), required=False, label=_('CPU model'))
|
||||
cpu_count = serializers.IntegerField(required=False, label=_('CPU count'))
|
||||
cpu_cores = serializers.IntegerField(required=False, label=_('CPU cores'))
|
||||
cpu_vcpus = serializers.IntegerField(required=False, label=_('CPU vcpus'))
|
||||
memory = serializers.CharField(max_length=64, allow_blank=True, required=False, label=_('Memory'))
|
||||
disk_total = serializers.CharField(max_length=1024, allow_blank=True, required=False, label=_('Disk total'))
|
||||
|
||||
distribution = serializers.CharField(max_length=128, allow_blank=True, required=False, label=_('OS'))
|
||||
distribution_version = serializers.CharField(max_length=16, allow_blank=True, required=False, label=_('OS version'))
|
||||
distribution_version = serializers.CharField(max_length=16, allow_blank=True, required=False, label=_('OS version'))
|
||||
arch = serializers.CharField(max_length=16, allow_blank=True, required=False, label=_('OS arch'))
|
||||
|
||||
|
||||
@@ -35,3 +36,5 @@ class HostSerializer(AssetSerializer):
|
||||
'label': _("IP/Host")
|
||||
},
|
||||
}
|
||||
|
||||
|
||||
|
||||
@@ -29,8 +29,7 @@ class LabelSerializer(BulkOrgResourceModelSerializer):
|
||||
|
||||
@classmethod
|
||||
def setup_eager_loading(cls, queryset):
|
||||
queryset = queryset.prefetch_related('assets') \
|
||||
.annotate(asset_count=Count('assets'))
|
||||
queryset = queryset.annotate(asset_count=Count('assets'))
|
||||
return queryset
|
||||
|
||||
|
||||
|
||||
@@ -1,5 +1,6 @@
|
||||
from django.utils.translation import gettext_lazy as _
|
||||
from rest_framework import serializers
|
||||
from django.core import validators
|
||||
|
||||
from assets.const.web import FillType
|
||||
from common.serializers import WritableNestedModelSerializer
|
||||
@@ -18,7 +19,7 @@ class ProtocolSettingSerializer(serializers.Serializer):
|
||||
("nla", "NLA"),
|
||||
]
|
||||
# RDP
|
||||
console = serializers.BooleanField(required=False, default=False)
|
||||
console = serializers.BooleanField(required=False)
|
||||
security = serializers.ChoiceField(choices=SECURITY_CHOICES, default="any")
|
||||
|
||||
# SFTP
|
||||
|
||||
@@ -1,11 +1,14 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
from urllib.parse import urlencode
|
||||
from urllib3.exceptions import MaxRetryError, LocationParseError
|
||||
|
||||
from kubernetes import client
|
||||
from kubernetes.client import api_client
|
||||
from kubernetes.client.api import core_v1_api
|
||||
from kubernetes.client.exceptions import ApiException
|
||||
|
||||
from common.utils import get_logger
|
||||
from common.exceptions import JMSException
|
||||
from ..const import CloudTypes, Category
|
||||
|
||||
logger = get_logger(__file__)
|
||||
@@ -17,8 +20,7 @@ class KubernetesClient:
|
||||
self.token = token
|
||||
self.proxy = proxy
|
||||
|
||||
@property
|
||||
def api(self):
|
||||
def get_api(self):
|
||||
configuration = client.Configuration()
|
||||
configuration.host = self.url
|
||||
configuration.proxy = self.proxy
|
||||
@@ -28,29 +30,64 @@ class KubernetesClient:
|
||||
api = core_v1_api.CoreV1Api(c)
|
||||
return api
|
||||
|
||||
def get_namespaces(self):
|
||||
namespaces = []
|
||||
resp = self.api.list_namespace()
|
||||
for ns in resp.items:
|
||||
namespaces.append(ns.metadata.name)
|
||||
return namespaces
|
||||
def get_namespace_list(self):
|
||||
api = self.get_api()
|
||||
namespace_list = []
|
||||
for ns in api.list_namespace().items:
|
||||
namespace_list.append(ns.metadata.name)
|
||||
return namespace_list
|
||||
|
||||
def get_pods(self, namespace):
|
||||
pods = []
|
||||
resp = self.api.list_namespaced_pod(namespace)
|
||||
for pd in resp.items:
|
||||
pods.append(pd.metadata.name)
|
||||
return pods
|
||||
def get_services(self):
|
||||
api = self.get_api()
|
||||
ret = api.list_service_for_all_namespaces(watch=False)
|
||||
for i in ret.items:
|
||||
print("%s \t%s \t%s \t%s \t%s \n" % (
|
||||
i.kind, i.metadata.namespace, i.metadata.name, i.spec.cluster_ip, i.spec.ports))
|
||||
|
||||
def get_containers(self, namespace, pod_name):
|
||||
containers = []
|
||||
resp = self.api.read_namespaced_pod(pod_name, namespace)
|
||||
for container in resp.spec.containers:
|
||||
containers.append(container.name)
|
||||
return containers
|
||||
def get_pod_info(self, namespace, pod):
|
||||
api = self.get_api()
|
||||
resp = api.read_namespaced_pod(namespace=namespace, name=pod)
|
||||
return resp
|
||||
|
||||
@staticmethod
|
||||
def get_proxy_url(asset):
|
||||
def get_pod_logs(self, namespace, pod):
|
||||
api = self.get_api()
|
||||
log_content = api.read_namespaced_pod_log(pod, namespace, pretty=True, tail_lines=200)
|
||||
return log_content
|
||||
|
||||
def get_pods(self):
|
||||
api = self.get_api()
|
||||
try:
|
||||
ret = api.list_pod_for_all_namespaces(watch=False, _request_timeout=(3, 3))
|
||||
except LocationParseError as e:
|
||||
logger.warning("Kubernetes API request url error: {}".format(e))
|
||||
raise JMSException(code='k8s_tree_error', detail=e)
|
||||
except MaxRetryError:
|
||||
msg = "Kubernetes API request timeout"
|
||||
logger.warning(msg)
|
||||
raise JMSException(code='k8s_tree_error', detail=msg)
|
||||
except ApiException as e:
|
||||
if e.status == 401:
|
||||
msg = "Kubernetes API request unauthorized"
|
||||
logger.warning(msg)
|
||||
else:
|
||||
msg = e
|
||||
logger.warning(msg)
|
||||
raise JMSException(code='k8s_tree_error', detail=msg)
|
||||
data = {}
|
||||
for i in ret.items:
|
||||
namespace = i.metadata.namespace
|
||||
pod_info = {
|
||||
'pod_name': i.metadata.name,
|
||||
'containers': [j.name for j in i.spec.containers]
|
||||
}
|
||||
if namespace in data:
|
||||
data[namespace].append(pod_info)
|
||||
else:
|
||||
data[namespace] = [pod_info, ]
|
||||
return data
|
||||
|
||||
@classmethod
|
||||
def get_proxy_url(cls, asset):
|
||||
if not asset.domain:
|
||||
return None
|
||||
|
||||
@@ -60,14 +97,11 @@ class KubernetesClient:
|
||||
return f'{gateway.address}:{gateway.port}'
|
||||
|
||||
@classmethod
|
||||
def run(cls, asset, secret, tp, *args):
|
||||
def get_kubernetes_data(cls, asset, secret):
|
||||
k8s_url = f'{asset.address}'
|
||||
proxy_url = cls.get_proxy_url(asset)
|
||||
k8s = cls(k8s_url, secret, proxy=proxy_url)
|
||||
func_name = f'get_{tp}s'
|
||||
if hasattr(k8s, func_name):
|
||||
return getattr(k8s, func_name)(*args)
|
||||
return []
|
||||
return k8s.get_pods()
|
||||
|
||||
|
||||
class KubernetesTree:
|
||||
@@ -83,15 +117,17 @@ class KubernetesTree:
|
||||
)
|
||||
return node
|
||||
|
||||
def as_namespace_node(self, name, tp):
|
||||
def as_namespace_node(self, name, tp, counts=0):
|
||||
i = urlencode({'namespace': name})
|
||||
pid = str(self.asset.id)
|
||||
name = f'{name}({counts})'
|
||||
node = self.create_tree_node(i, pid, name, tp, icon='cloud')
|
||||
return node
|
||||
|
||||
def as_pod_tree_node(self, namespace, name, tp):
|
||||
def as_pod_tree_node(self, namespace, name, tp, counts=0):
|
||||
pid = urlencode({'namespace': namespace})
|
||||
i = urlencode({'namespace': namespace, 'pod': name})
|
||||
name = f'{name}({counts})'
|
||||
node = self.create_tree_node(i, pid, name, tp, icon='cloud')
|
||||
return node
|
||||
|
||||
@@ -126,26 +162,30 @@ class KubernetesTree:
|
||||
|
||||
def async_tree_node(self, namespace, pod):
|
||||
tree = []
|
||||
data = KubernetesClient.get_kubernetes_data(self.asset, self.secret)
|
||||
if not data:
|
||||
return tree
|
||||
|
||||
if pod:
|
||||
tp = 'container'
|
||||
containers = KubernetesClient.run(
|
||||
self.asset, self.secret, tp, namespace, pod
|
||||
)
|
||||
for container in containers:
|
||||
for container in next(
|
||||
filter(
|
||||
lambda x: x['pod_name'] == pod, data[namespace]
|
||||
)
|
||||
)['containers']:
|
||||
container_node = self.as_container_tree_node(
|
||||
namespace, pod, container, tp
|
||||
namespace, pod, container, 'container'
|
||||
)
|
||||
tree.append(container_node)
|
||||
elif namespace:
|
||||
tp = 'pod'
|
||||
pods = KubernetesClient.run(self.asset, self.secret, tp, namespace)
|
||||
for pod in pods:
|
||||
pod_node = self.as_pod_tree_node(namespace, pod, tp)
|
||||
tree.append(pod_node)
|
||||
for pod in data[namespace]:
|
||||
pod_nodes = self.as_pod_tree_node(
|
||||
namespace, pod['pod_name'], 'pod', len(pod['containers'])
|
||||
)
|
||||
tree.append(pod_nodes)
|
||||
else:
|
||||
tp = 'namespace'
|
||||
namespaces = KubernetesClient.run(self.asset, self.secret, tp)
|
||||
for namespace in namespaces:
|
||||
namespace_node = self.as_namespace_node(namespace, tp)
|
||||
for namespace, pods in data.items():
|
||||
namespace_node = self.as_namespace_node(
|
||||
namespace, 'namespace', len(pods)
|
||||
)
|
||||
tree.append(namespace_node)
|
||||
return tree
|
||||
|
||||
@@ -10,7 +10,6 @@ from rest_framework.permissions import IsAuthenticated
|
||||
from common.drf.filters import DatetimeRangeFilter
|
||||
from common.plugins.es import QuerySet as ESQuerySet
|
||||
from common.utils import is_uuid
|
||||
from common.utils import lazyproperty
|
||||
from orgs.mixins.api import OrgReadonlyModelViewSet, OrgModelViewSet
|
||||
from orgs.utils import current_org, tmp_to_root_org
|
||||
from orgs.models import Organization
|
||||
@@ -144,19 +143,13 @@ class OperateLogViewSet(OrgReadonlyModelViewSet):
|
||||
search_fields = ['resource', 'user']
|
||||
ordering = ['-datetime']
|
||||
|
||||
@lazyproperty
|
||||
def is_action_detail(self):
|
||||
return self.detail and self.request.query_params.get('type') == 'action_detail'
|
||||
|
||||
def get_serializer_class(self):
|
||||
if self.is_action_detail:
|
||||
if self.request.query_params.get('type') == 'action_detail':
|
||||
return OperateLogActionDetailSerializer
|
||||
return super().get_serializer_class()
|
||||
|
||||
def get_queryset(self):
|
||||
org_q = Q(org_id=current_org.id)
|
||||
if self.is_action_detail:
|
||||
org_q |= Q(org_id=Organization.SYSTEM_ID)
|
||||
org_q = Q(org_id=Organization.SYSTEM_ID) | Q(org_id=current_org.id)
|
||||
with tmp_to_root_org():
|
||||
qs = OperateLog.objects.filter(org_q)
|
||||
es_config = settings.OPERATE_LOG_ELASTICSEARCH_CONFIG
|
||||
|
||||
@@ -4,6 +4,7 @@ from django.db import transaction
|
||||
from django.core.cache import cache
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
|
||||
from users.models import User
|
||||
from common.utils import get_request_ip, get_logger
|
||||
from common.utils.timezone import as_current_tz
|
||||
from common.utils.encode import Singleton
|
||||
|
||||
@@ -2,7 +2,7 @@
|
||||
#
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
from rest_framework import serializers
|
||||
from orgs.mixins.serializers import BulkOrgResourceModelSerializer
|
||||
|
||||
from audits.backends.db import OperateLogStore
|
||||
from common.serializers.fields import LabeledChoiceField
|
||||
from common.utils import reverse, i18n_trans
|
||||
@@ -78,7 +78,7 @@ class OperateLogActionDetailSerializer(serializers.ModelSerializer):
|
||||
return data
|
||||
|
||||
|
||||
class OperateLogSerializer(BulkOrgResourceModelSerializer):
|
||||
class OperateLogSerializer(serializers.ModelSerializer):
|
||||
action = LabeledChoiceField(choices=ActionChoices.choices, label=_("Action"))
|
||||
resource = serializers.SerializerMethodField(label=_("Resource"))
|
||||
resource_type = serializers.SerializerMethodField(label=_('Resource Type'))
|
||||
|
||||
@@ -1,15 +1,13 @@
|
||||
import codecs
|
||||
import copy
|
||||
import csv
|
||||
|
||||
from itertools import chain
|
||||
from datetime import datetime
|
||||
|
||||
from django.db import models
|
||||
from django.http import HttpResponse
|
||||
|
||||
from common.utils.timezone import as_current_tz
|
||||
from common.utils import validate_ip, get_ip_city, get_logger
|
||||
from settings.serializers import SettingsSerializer
|
||||
from .const import DEFAULT_CITY
|
||||
|
||||
logger = get_logger(__name__)
|
||||
@@ -72,8 +70,6 @@ def _get_instance_field_value(
|
||||
f.verbose_name = 'id'
|
||||
elif isinstance(value, (list, dict)):
|
||||
value = copy.deepcopy(value)
|
||||
elif isinstance(value, datetime):
|
||||
value = as_current_tz(value).strftime('%Y-%m-%d %H:%M:%S')
|
||||
elif isinstance(f, models.OneToOneField) and isinstance(value, models.Model):
|
||||
nested_data = _get_instance_field_value(
|
||||
value, include_model_fields, model_need_continue_fields, ('id',)
|
||||
|
||||
@@ -24,7 +24,7 @@ from orgs.mixins.api import RootOrgViewMixin
|
||||
from perms.models import ActionChoices
|
||||
from terminal.connect_methods import NativeClient, ConnectMethodUtil
|
||||
from terminal.models import EndpointRule
|
||||
from ..models import ConnectionToken, date_expired_default
|
||||
from ..models import ConnectionToken
|
||||
from ..serializers import (
|
||||
ConnectionTokenSerializer, ConnectionTokenSecretSerializer,
|
||||
SuperConnectionTokenSerializer, ConnectTokenAppletOptionSerializer
|
||||
@@ -172,7 +172,6 @@ class ExtraActionApiMixin(RDPFileClientProtocolURLMixin):
|
||||
get_object: callable
|
||||
get_serializer: callable
|
||||
perform_create: callable
|
||||
validate_exchange_token: callable
|
||||
|
||||
@action(methods=['POST', 'GET'], detail=True, url_path='rdp-file')
|
||||
def get_rdp_file(self, *args, **kwargs):
|
||||
@@ -205,18 +204,6 @@ class ExtraActionApiMixin(RDPFileClientProtocolURLMixin):
|
||||
instance.expire()
|
||||
return Response(status=status.HTTP_204_NO_CONTENT)
|
||||
|
||||
@action(methods=['POST'], detail=False)
|
||||
def exchange(self, request, *args, **kwargs):
|
||||
pk = request.data.get('id', None) or request.data.get('pk', None)
|
||||
# 只能兑换自己使用的 Token
|
||||
instance = get_object_or_404(ConnectionToken, pk=pk, user=request.user)
|
||||
instance.id = None
|
||||
self.validate_exchange_token(instance)
|
||||
instance.date_expired = date_expired_default()
|
||||
instance.save()
|
||||
serializer = self.get_serializer(instance)
|
||||
return Response(serializer.data, status=status.HTTP_201_CREATED)
|
||||
|
||||
|
||||
class ConnectionTokenViewSet(ExtraActionApiMixin, RootOrgViewMixin, JMSModelViewSet):
|
||||
filterset_fields = (
|
||||
@@ -230,7 +217,6 @@ class ConnectionTokenViewSet(ExtraActionApiMixin, RootOrgViewMixin, JMSModelView
|
||||
'list': 'authentication.view_connectiontoken',
|
||||
'retrieve': 'authentication.view_connectiontoken',
|
||||
'create': 'authentication.add_connectiontoken',
|
||||
'exchange': 'authentication.add_connectiontoken',
|
||||
'expire': 'authentication.change_connectiontoken',
|
||||
'get_rdp_file': 'authentication.add_connectiontoken',
|
||||
'get_client_protocol_url': 'authentication.add_connectiontoken',
|
||||
@@ -254,24 +240,10 @@ class ConnectionTokenViewSet(ExtraActionApiMixin, RootOrgViewMixin, JMSModelView
|
||||
user = self.get_user(serializer)
|
||||
asset = data.get('asset')
|
||||
account_name = data.get('account')
|
||||
_data = self._validate(user, asset, account_name)
|
||||
data.update(_data)
|
||||
return serializer
|
||||
|
||||
def validate_exchange_token(self, token):
|
||||
user = token.user
|
||||
asset = token.asset
|
||||
account_name = token.account
|
||||
_data = self._validate(user, asset, account_name)
|
||||
for k, v in _data.items():
|
||||
setattr(token, k, v)
|
||||
return token
|
||||
|
||||
def _validate(self, user, asset, account_name):
|
||||
data = dict()
|
||||
data['org_id'] = asset.org_id
|
||||
data['user'] = user
|
||||
data['value'] = random_string(16)
|
||||
|
||||
account = self._validate_perm(user, asset, account_name)
|
||||
if account.has_secret:
|
||||
data['input_secret'] = ''
|
||||
@@ -285,7 +257,8 @@ class ConnectionTokenViewSet(ExtraActionApiMixin, RootOrgViewMixin, JMSModelView
|
||||
if ticket:
|
||||
data['from_ticket'] = ticket
|
||||
data['is_active'] = False
|
||||
return data
|
||||
|
||||
return account
|
||||
|
||||
@staticmethod
|
||||
def _validate_perm(user, asset, account_name):
|
||||
|
||||
@@ -222,8 +222,7 @@ class ConnectionToken(JMSOrgBaseModel):
|
||||
'secret_type': account.secret_type,
|
||||
'secret': account.secret or self.input_secret,
|
||||
'su_from': account.su_from,
|
||||
'org_id': account.org_id,
|
||||
'privileged': account.privileged
|
||||
'org_id': account.org_id
|
||||
}
|
||||
return Account(**data)
|
||||
|
||||
|
||||
@@ -60,7 +60,7 @@ class FeiShuQRMixin(UserConfirmRequiredExceptionMixin, PermissionsMixin, View):
|
||||
'state': state,
|
||||
'redirect_uri': redirect_uri,
|
||||
}
|
||||
url = URL().authen + '?' + urlencode(params)
|
||||
url = URL.AUTHEN + '?' + urlencode(params)
|
||||
return url
|
||||
|
||||
@staticmethod
|
||||
|
||||
@@ -6,7 +6,6 @@ import os
|
||||
import datetime
|
||||
from typing import Callable
|
||||
|
||||
from django.db import IntegrityError
|
||||
from django.templatetags.static import static
|
||||
from django.contrib.auth import login as auth_login, logout as auth_logout
|
||||
from django.http import HttpResponse, HttpRequest
|
||||
@@ -230,23 +229,6 @@ class UserLoginView(mixins.AuthMixin, UserLoginContextMixin, FormView):
|
||||
) as e:
|
||||
form.add_error('code', e.msg)
|
||||
return super().form_invalid(form)
|
||||
except (IntegrityError,) as e:
|
||||
# (1062, "Duplicate entry 'youtester001@example.com' for key 'users_user.email'")
|
||||
error = str(e)
|
||||
if len(e.args) < 2:
|
||||
form.add_error(None, error)
|
||||
return super().form_invalid(form)
|
||||
|
||||
msg_list = e.args[1].split("'")
|
||||
if len(msg_list) < 4:
|
||||
form.add_error(None, error)
|
||||
return super().form_invalid(form)
|
||||
|
||||
email, field = msg_list[1], msg_list[3]
|
||||
if field == 'users_user.email':
|
||||
error = _('User email already exists ({})').format(email)
|
||||
form.add_error(None, error)
|
||||
return super().form_invalid(form)
|
||||
self.clear_rsa_key()
|
||||
return self.redirect_to_guard_view()
|
||||
|
||||
|
||||
@@ -2,3 +2,4 @@ from __future__ import absolute_import
|
||||
|
||||
# This will make sure the app is always imported when
|
||||
# Django starts so that shared_task will use this app.
|
||||
|
||||
|
||||
@@ -3,12 +3,13 @@
|
||||
from typing import Callable
|
||||
|
||||
from django.utils.translation import ugettext as _
|
||||
from rest_framework.response import Response
|
||||
from rest_framework.decorators import action
|
||||
from rest_framework.request import Request
|
||||
from rest_framework.response import Response
|
||||
|
||||
from common.const.http import POST
|
||||
|
||||
|
||||
__all__ = ['SuggestionMixin', 'RenderToJsonMixin']
|
||||
|
||||
|
||||
|
||||
@@ -1,15 +1,11 @@
|
||||
import abc
|
||||
import codecs
|
||||
import json
|
||||
import re
|
||||
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
import codecs
|
||||
from rest_framework import serializers
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
from rest_framework.parsers import BaseParser
|
||||
from rest_framework import status
|
||||
from rest_framework.exceptions import ParseError, APIException
|
||||
from rest_framework.parsers import BaseParser
|
||||
|
||||
from common.serializers.fields import ObjectRelatedField
|
||||
from common.utils import get_logger
|
||||
|
||||
logger = get_logger(__file__)
|
||||
@@ -22,11 +18,11 @@ class FileContentOverflowedError(APIException):
|
||||
|
||||
|
||||
class BaseFileParser(BaseParser):
|
||||
|
||||
FILE_CONTENT_MAX_LENGTH = 1024 * 1024 * 10
|
||||
|
||||
serializer_cls = None
|
||||
serializer_fields = None
|
||||
obj_pattern = re.compile(r'^(.+)\(([a-z0-9-]+)\)$')
|
||||
|
||||
def check_content_length(self, meta):
|
||||
content_length = int(meta.get('CONTENT_LENGTH', meta.get('HTTP_CONTENT_LENGTH', 0)))
|
||||
@@ -78,7 +74,7 @@ class BaseFileParser(BaseParser):
|
||||
return s.translate(trans_table)
|
||||
|
||||
@classmethod
|
||||
def load_row(cls, row):
|
||||
def process_row(cls, row):
|
||||
"""
|
||||
构建json数据前的行处理
|
||||
"""
|
||||
@@ -88,63 +84,33 @@ class BaseFileParser(BaseParser):
|
||||
col = cls._replace_chinese_quote(col)
|
||||
# 列表/字典转换
|
||||
if isinstance(col, str) and (
|
||||
(col.startswith('[') and col.endswith(']')) or
|
||||
(col.startswith('[') and col.endswith(']'))
|
||||
or
|
||||
(col.startswith("{") and col.endswith("}"))
|
||||
):
|
||||
try:
|
||||
col = json.loads(col)
|
||||
except json.JSONDecodeError as e:
|
||||
logger.error('Json load error: ', e)
|
||||
logger.error('col: ', col)
|
||||
col = json.loads(col)
|
||||
new_row.append(col)
|
||||
return new_row
|
||||
|
||||
def id_name_to_obj(self, v):
|
||||
if not v or not isinstance(v, str):
|
||||
return v
|
||||
matched = self.obj_pattern.match(v)
|
||||
if not matched:
|
||||
return v
|
||||
obj_name, obj_id = matched.groups()
|
||||
if len(obj_id) < 36:
|
||||
obj_id = int(obj_id)
|
||||
return {'pk': obj_id, 'name': obj_name}
|
||||
|
||||
def parse_value(self, field, value):
|
||||
if value == '-' and field and field.allow_null:
|
||||
return None
|
||||
elif hasattr(field, 'to_file_internal_value'):
|
||||
value = field.to_file_internal_value(value)
|
||||
elif isinstance(field, serializers.BooleanField):
|
||||
value = value.lower() in ['true', '1', 'yes']
|
||||
elif isinstance(field, serializers.ChoiceField):
|
||||
value = value
|
||||
elif isinstance(field, ObjectRelatedField):
|
||||
if field.many:
|
||||
value = [self.id_name_to_obj(v) for v in value]
|
||||
else:
|
||||
value = self.id_name_to_obj(value)
|
||||
elif isinstance(field, serializers.ListSerializer):
|
||||
value = [self.parse_value(field.child, v) for v in value]
|
||||
elif isinstance(field, serializers.Serializer):
|
||||
value = self.id_name_to_obj(value)
|
||||
elif isinstance(field, serializers.ManyRelatedField):
|
||||
value = [self.parse_value(field.child_relation, v) for v in value]
|
||||
elif isinstance(field, serializers.ListField):
|
||||
value = [self.parse_value(field.child, v) for v in value]
|
||||
|
||||
return value
|
||||
|
||||
def process_row_data(self, row_data):
|
||||
"""
|
||||
构建json数据后的行数据处理
|
||||
"""
|
||||
new_row = {}
|
||||
new_row_data = {}
|
||||
serializer_fields = self.serializer_fields
|
||||
for k, v in row_data.items():
|
||||
field = self.serializer_fields.get(k)
|
||||
v = self.parse_value(field, v)
|
||||
new_row[k] = v
|
||||
return new_row
|
||||
if type(v) in [list, dict, int, bool] or (isinstance(v, str) and k.strip() and v.strip()):
|
||||
# 处理类似disk_info为字符串的'{}'的问题
|
||||
if not isinstance(v, str) and isinstance(serializer_fields[k], serializers.CharField):
|
||||
v = str(v)
|
||||
# 处理 BooleanField 的问题, 导出是 'True', 'False'
|
||||
if isinstance(v, str) and v.strip().lower() == 'true':
|
||||
v = True
|
||||
elif isinstance(v, str) and v.strip().lower() == 'false':
|
||||
v = False
|
||||
|
||||
new_row_data[k] = v
|
||||
return new_row_data
|
||||
|
||||
def generate_data(self, fields_name, rows):
|
||||
data = []
|
||||
@@ -152,7 +118,7 @@ class BaseFileParser(BaseParser):
|
||||
# 空行不处理
|
||||
if not any(row):
|
||||
continue
|
||||
row = self.load_row(row)
|
||||
row = self.process_row(row)
|
||||
row_data = dict(zip(fields_name, row))
|
||||
row_data = self.process_row_data(row_data)
|
||||
data.append(row_data)
|
||||
@@ -173,6 +139,7 @@ class BaseFileParser(BaseParser):
|
||||
raise ParseError('The resource does not support imports!')
|
||||
|
||||
self.check_content_length(meta)
|
||||
|
||||
try:
|
||||
stream_data = self.get_stream_data(stream)
|
||||
rows = self.generate_rows(stream_data)
|
||||
@@ -181,7 +148,6 @@ class BaseFileParser(BaseParser):
|
||||
|
||||
# 给 `common.mixins.api.RenderToJsonMixin` 提供,暂时只能耦合
|
||||
column_title_field_pairs = list(zip(column_titles, field_names))
|
||||
column_title_field_pairs = [(k, v) for k, v in column_title_field_pairs if k and v]
|
||||
if not hasattr(request, 'jms_context'):
|
||||
request.jms_context = {}
|
||||
request.jms_context['column_title_field_pairs'] = column_title_field_pairs
|
||||
@@ -191,3 +157,4 @@ class BaseFileParser(BaseParser):
|
||||
except Exception as e:
|
||||
logger.error(e, exc_info=True)
|
||||
raise ParseError(_('Parse file error: {}').format(e))
|
||||
|
||||
|
||||
@@ -1,17 +1,13 @@
|
||||
import pyexcel
|
||||
from django.utils.translation import gettext as _
|
||||
|
||||
from .base import BaseFileParser
|
||||
|
||||
|
||||
class ExcelFileParser(BaseFileParser):
|
||||
|
||||
media_type = 'text/xlsx'
|
||||
|
||||
def generate_rows(self, stream_data):
|
||||
try:
|
||||
workbook = pyexcel.get_book(file_type='xlsx', file_content=stream_data)
|
||||
except Exception:
|
||||
raise Exception(_('Invalid excel file'))
|
||||
workbook = pyexcel.get_book(file_type='xlsx', file_content=stream_data)
|
||||
# 默认获取第一个工作表sheet
|
||||
sheet = workbook.sheet_by_index(0)
|
||||
rows = sheet.rows()
|
||||
|
||||
@@ -1,11 +1,8 @@
|
||||
import abc
|
||||
from datetime import datetime
|
||||
|
||||
from rest_framework import serializers
|
||||
from rest_framework.renderers import BaseRenderer
|
||||
from rest_framework.utils import encoders, json
|
||||
|
||||
from common.serializers.fields import ObjectRelatedField, LabeledChoiceField
|
||||
from common.utils import get_logger
|
||||
|
||||
logger = get_logger(__file__)
|
||||
@@ -41,27 +38,18 @@ class BaseFileRenderer(BaseRenderer):
|
||||
def get_rendered_fields(self):
|
||||
fields = self.serializer.fields
|
||||
if self.template == 'import':
|
||||
fields = [v for k, v in fields.items() if not v.read_only and k != "org_id" and k != 'id']
|
||||
return [v for k, v in fields.items() if not v.read_only and k != "org_id" and k != 'id']
|
||||
elif self.template == 'update':
|
||||
fields = [v for k, v in fields.items() if not v.read_only and k != "org_id"]
|
||||
return [v for k, v in fields.items() if not v.read_only and k != "org_id"]
|
||||
else:
|
||||
fields = [v for k, v in fields.items() if not v.write_only and k != "org_id"]
|
||||
|
||||
meta = getattr(self.serializer, 'Meta', None)
|
||||
if meta:
|
||||
fields_unexport = getattr(meta, 'fields_unexport', [])
|
||||
fields = [v for v in fields if v.field_name not in fields_unexport]
|
||||
return fields
|
||||
return [v for k, v in fields.items() if not v.write_only and k != "org_id"]
|
||||
|
||||
@staticmethod
|
||||
def get_column_titles(render_fields):
|
||||
titles = []
|
||||
for field in render_fields:
|
||||
name = field.label
|
||||
if field.required:
|
||||
name = '*' + name
|
||||
titles.append(name)
|
||||
return titles
|
||||
return [
|
||||
'*{}'.format(field.label) if field.required else str(field.label)
|
||||
for field in render_fields
|
||||
]
|
||||
|
||||
def process_data(self, data):
|
||||
results = data['results'] if 'results' in data else data
|
||||
@@ -71,6 +59,7 @@ class BaseFileRenderer(BaseRenderer):
|
||||
|
||||
if self.template == 'import':
|
||||
results = [results[0]] if results else results
|
||||
|
||||
else:
|
||||
# 限制数据数量
|
||||
results = results[:10000]
|
||||
@@ -79,53 +68,17 @@ class BaseFileRenderer(BaseRenderer):
|
||||
return results
|
||||
|
||||
@staticmethod
|
||||
def to_id_name(value):
|
||||
if value is None:
|
||||
return '-'
|
||||
pk = str(value.get('id', '') or value.get('pk', ''))
|
||||
name = value.get('name') or value.get('display_name', '')
|
||||
return '{}({})'.format(name, pk)
|
||||
|
||||
@staticmethod
|
||||
def to_choice_name(value):
|
||||
if value is None:
|
||||
return '-'
|
||||
value = value.get('value', '')
|
||||
return value
|
||||
|
||||
def render_value(self, field, value):
|
||||
if value is None:
|
||||
value = '-'
|
||||
elif hasattr(field, 'to_file_representation'):
|
||||
value = field.to_file_representation(value)
|
||||
elif isinstance(value, bool):
|
||||
value = 'Yes' if value else 'No'
|
||||
elif isinstance(field, LabeledChoiceField):
|
||||
value = value.get('value', '')
|
||||
elif isinstance(field, ObjectRelatedField):
|
||||
if field.many:
|
||||
value = [self.to_id_name(v) for v in value]
|
||||
else:
|
||||
value = self.to_id_name(value)
|
||||
elif isinstance(field, serializers.ListSerializer):
|
||||
value = [self.render_value(field.child, v) for v in value]
|
||||
elif isinstance(field, serializers.Serializer) and value.get('id'):
|
||||
value = self.to_id_name(value)
|
||||
elif isinstance(field, serializers.ManyRelatedField):
|
||||
value = [self.render_value(field.child_relation, v) for v in value]
|
||||
elif isinstance(field, serializers.ListField):
|
||||
value = [self.render_value(field.child, v) for v in value]
|
||||
|
||||
if not isinstance(value, str):
|
||||
value = json.dumps(value, cls=encoders.JSONEncoder, ensure_ascii=False)
|
||||
return str(value)
|
||||
|
||||
def generate_rows(self, data, render_fields):
|
||||
def generate_rows(data, render_fields):
|
||||
for item in data:
|
||||
row = []
|
||||
for field in render_fields:
|
||||
value = item.get(field.field_name)
|
||||
value = self.render_value(field, value)
|
||||
if value is None:
|
||||
value = ''
|
||||
elif isinstance(value, dict):
|
||||
value = json.dumps(value, ensure_ascii=False)
|
||||
else:
|
||||
value = str(value)
|
||||
row.append(value)
|
||||
yield row
|
||||
|
||||
@@ -148,9 +101,6 @@ class BaseFileRenderer(BaseRenderer):
|
||||
def get_rendered_value(self):
|
||||
raise NotImplementedError
|
||||
|
||||
def after_render(self):
|
||||
pass
|
||||
|
||||
def render(self, data, accepted_media_type=None, renderer_context=None):
|
||||
if data is None:
|
||||
return bytes()
|
||||
@@ -179,10 +129,11 @@ class BaseFileRenderer(BaseRenderer):
|
||||
self.initial_writer()
|
||||
self.write_column_titles(column_titles)
|
||||
self.write_rows(rows)
|
||||
self.after_render()
|
||||
value = self.get_rendered_value()
|
||||
except Exception as e:
|
||||
logger.debug(e, exc_info=True)
|
||||
value = 'Render error! ({})'.format(self.media_type).encode('utf-8')
|
||||
return value
|
||||
|
||||
return value
|
||||
|
||||
|
||||
@@ -1,6 +1,6 @@
|
||||
from openpyxl import Workbook
|
||||
from openpyxl.cell.cell import ILLEGAL_CHARACTERS_RE
|
||||
from openpyxl.writer.excel import save_virtual_workbook
|
||||
from openpyxl.cell.cell import ILLEGAL_CHARACTERS_RE
|
||||
|
||||
from .base import BaseFileRenderer
|
||||
|
||||
@@ -19,26 +19,12 @@ class ExcelFileRenderer(BaseFileRenderer):
|
||||
|
||||
def write_row(self, row):
|
||||
self.row_count += 1
|
||||
self.ws.row_dimensions[self.row_count].height = 20
|
||||
column_count = 0
|
||||
for cell_value in row:
|
||||
# 处理非法字符
|
||||
column_count += 1
|
||||
cell_value = ILLEGAL_CHARACTERS_RE.sub(r'', str(cell_value))
|
||||
self.ws.cell(row=self.row_count, column=column_count, value=str(cell_value))
|
||||
|
||||
def after_render(self):
|
||||
for col in self.ws.columns:
|
||||
max_length = 0
|
||||
column = col[0].column_letter
|
||||
for cell in col:
|
||||
if len(str(cell.value)) > max_length:
|
||||
max_length = len(cell.value)
|
||||
adjusted_width = (max_length + 2) * 1.0
|
||||
adjusted_width = 300 if adjusted_width > 300 else adjusted_width
|
||||
adjusted_width = 30 if adjusted_width < 30 else adjusted_width
|
||||
self.ws.column_dimensions[column].width = adjusted_width
|
||||
self.wb.save('/tmp/test.xlsx')
|
||||
cell_value = ILLEGAL_CHARACTERS_RE.sub(r'', cell_value)
|
||||
self.ws.cell(row=self.row_count, column=column_count, value=cell_value)
|
||||
|
||||
def get_rendered_value(self):
|
||||
value = save_virtual_workbook(self.wb)
|
||||
|
||||
@@ -1,10 +1,7 @@
|
||||
from werkzeug.local import Local
|
||||
|
||||
from django.utils import translation
|
||||
|
||||
|
||||
thread_local = Local()
|
||||
encrypted_field_set = {'password', 'secret'}
|
||||
encrypted_field_set = set()
|
||||
|
||||
|
||||
def _find(attr):
|
||||
@@ -13,5 +10,4 @@ def _find(attr):
|
||||
|
||||
def add_encrypted_field_set(label):
|
||||
if label:
|
||||
with translation.override('en'):
|
||||
encrypted_field_set.add(str(label))
|
||||
encrypted_field_set.add(str(label))
|
||||
|
||||
@@ -114,28 +114,26 @@ class ES(object):
|
||||
self._ensure_index_exists()
|
||||
|
||||
def _ensure_index_exists(self):
|
||||
info = self.es.info()
|
||||
version = info['version']['number'].split('.')[0]
|
||||
if version == '6':
|
||||
mappings = {'mappings': {'data': {'properties': self.properties}}}
|
||||
else:
|
||||
mappings = {'mappings': {'properties': self.properties}}
|
||||
|
||||
if self.is_index_by_date:
|
||||
mappings['aliases'] = {
|
||||
self.query_index: {}
|
||||
}
|
||||
|
||||
try:
|
||||
info = self.es.info()
|
||||
version = info['version']['number'].split('.')[0]
|
||||
if version == '6':
|
||||
mappings = {'mappings': {'data': {'properties': self.properties}}}
|
||||
self.es.indices.create(self.index, body=mappings)
|
||||
return
|
||||
except RequestError as e:
|
||||
if e.error == 'resource_already_exists_exception':
|
||||
logger.warning(e)
|
||||
else:
|
||||
mappings = {'mappings': {'properties': self.properties}}
|
||||
|
||||
if self.is_index_by_date:
|
||||
mappings['aliases'] = {
|
||||
self.query_index: {}
|
||||
}
|
||||
|
||||
try:
|
||||
self.es.indices.create(self.index, body=mappings)
|
||||
except RequestError as e:
|
||||
if e.error == 'resource_already_exists_exception':
|
||||
logger.warning(e)
|
||||
else:
|
||||
logger.exception(e)
|
||||
except Exception as e:
|
||||
logger.error(e, exc_info=True)
|
||||
logger.exception(e)
|
||||
|
||||
def make_data(self, data):
|
||||
return []
|
||||
|
||||
@@ -3,7 +3,6 @@ import json
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
from rest_framework.exceptions import APIException
|
||||
|
||||
from django.conf import settings
|
||||
from common.utils.common import get_logger
|
||||
from common.sdk.im.utils import digest
|
||||
from common.sdk.im.mixin import RequestMixin, BaseRequest
|
||||
@@ -12,30 +11,14 @@ logger = get_logger(__name__)
|
||||
|
||||
|
||||
class URL:
|
||||
AUTHEN = 'https://open.feishu.cn/open-apis/authen/v1/index'
|
||||
|
||||
GET_TOKEN = 'https://open.feishu.cn/open-apis/auth/v3/tenant_access_token/internal/'
|
||||
|
||||
# https://open.feishu.cn/document/ukTMukTMukTM/uEDO4UjLxgDO14SM4gTN
|
||||
@property
|
||||
def host(self):
|
||||
if settings.FEISHU_VERSION == 'feishu':
|
||||
h = 'https://open.feishu.cn'
|
||||
else:
|
||||
h = 'https://open.larksuite.com'
|
||||
return h
|
||||
GET_USER_INFO_BY_CODE = 'https://open.feishu.cn/open-apis/authen/v1/access_token'
|
||||
|
||||
@property
|
||||
def authen(self):
|
||||
return f'{self.host}/open-apis/authen/v1/index'
|
||||
|
||||
@property
|
||||
def get_token(self):
|
||||
return f'{self.host}/open-apis/auth/v3/tenant_access_token/internal/'
|
||||
|
||||
@property
|
||||
def get_user_info_by_code(self):
|
||||
return f'{self.host}/open-apis/authen/v1/access_token'
|
||||
|
||||
@property
|
||||
def send_message(self):
|
||||
return f'{self.host}/open-apis/im/v1/messages'
|
||||
SEND_MESSAGE = 'https://open.feishu.cn/open-apis/im/v1/messages'
|
||||
|
||||
|
||||
class ErrorCode:
|
||||
@@ -68,7 +51,7 @@ class FeishuRequests(BaseRequest):
|
||||
|
||||
def request_access_token(self):
|
||||
data = {'app_id': self._app_id, 'app_secret': self._app_secret}
|
||||
response = self.raw_request('post', url=URL().get_token, data=data)
|
||||
response = self.raw_request('post', url=URL.GET_TOKEN, data=data)
|
||||
self.check_errcode_is_0(response)
|
||||
|
||||
access_token = response['tenant_access_token']
|
||||
@@ -103,7 +86,7 @@ class FeiShu(RequestMixin):
|
||||
'code': code
|
||||
}
|
||||
|
||||
data = self._requests.post(URL().get_user_info_by_code, json=body, check_errcode_is_0=False)
|
||||
data = self._requests.post(URL.GET_USER_INFO_BY_CODE, json=body, check_errcode_is_0=False)
|
||||
|
||||
self._requests.check_errcode_is_0(data)
|
||||
return data['data']['user_id']
|
||||
@@ -124,7 +107,7 @@ class FeiShu(RequestMixin):
|
||||
|
||||
try:
|
||||
logger.info(f'Feishu send text: user_ids={user_ids} msg={msg}')
|
||||
self._requests.post(URL().send_message, params=params, json=body)
|
||||
self._requests.post(URL.SEND_MESSAGE, params=params, json=body)
|
||||
except APIException as e:
|
||||
# 只处理可预知的错误
|
||||
logger.exception(e)
|
||||
|
||||
@@ -1,6 +1,5 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
#
|
||||
import phonenumbers
|
||||
from django.core.exceptions import ObjectDoesNotExist
|
||||
from django.utils.translation import gettext_lazy as _
|
||||
from rest_framework import serializers
|
||||
@@ -18,7 +17,6 @@ __all__ = [
|
||||
"BitChoicesField",
|
||||
"TreeChoicesField",
|
||||
"LabeledMultipleChoiceField",
|
||||
"PhoneField",
|
||||
]
|
||||
|
||||
|
||||
@@ -203,11 +201,3 @@ class BitChoicesField(TreeChoicesField):
|
||||
value = self.to_internal_value(data)
|
||||
self.run_validators(value)
|
||||
return value
|
||||
|
||||
|
||||
class PhoneField(serializers.CharField):
|
||||
def to_representation(self, value):
|
||||
if value:
|
||||
phone = phonenumbers.parse(value, 'CN')
|
||||
value = {'code': '+%s' % phone.country_code, 'phone': phone.national_number}
|
||||
return value
|
||||
|
||||
@@ -55,11 +55,9 @@ class BulkSerializerMixin(object):
|
||||
# add update_lookup_field field back to validated data
|
||||
# since super by default strips out read-only fields
|
||||
# hence id will no longer be present in validated_data
|
||||
if all([
|
||||
isinstance(self.root, BulkListSerializer),
|
||||
id_attr,
|
||||
request_method in ('PUT', 'PATCH')
|
||||
]):
|
||||
if all((isinstance(self.root, BulkListSerializer),
|
||||
id_attr,
|
||||
request_method in ('PUT', 'PATCH'))):
|
||||
id_field = self.fields.get("id") or self.fields.get('pk')
|
||||
if data.get("id"):
|
||||
id_value = id_field.to_internal_value(data.get("id"))
|
||||
@@ -137,7 +135,7 @@ class BulkListSerializerMixin:
|
||||
pk = item["pk"]
|
||||
else:
|
||||
raise ValidationError("id or pk not in data")
|
||||
child = self.instance.get(pk=pk)
|
||||
child = self.instance.get(id=pk)
|
||||
self.child.instance = child
|
||||
self.child.initial_data = item
|
||||
# raw
|
||||
|
||||
@@ -32,7 +32,7 @@ class Counter:
|
||||
return self.counter == other.counter
|
||||
|
||||
|
||||
def digest_sql_query():
|
||||
def on_request_finished_logging_db_query(sender, **kwargs):
|
||||
queries = connection.queries
|
||||
counters = defaultdict(Counter)
|
||||
table_queries = defaultdict(list)
|
||||
@@ -79,9 +79,6 @@ def digest_sql_query():
|
||||
counter.counter, counter.time, name)
|
||||
)
|
||||
|
||||
|
||||
def on_request_finished_logging_db_query(sender, **kwargs):
|
||||
digest_sql_query()
|
||||
on_request_finished_release_local(sender, **kwargs)
|
||||
|
||||
|
||||
|
||||
@@ -108,7 +108,7 @@ class Subscription:
|
||||
try:
|
||||
self.sub.close()
|
||||
except Exception as e:
|
||||
logger.debug('Unsubscribe msg error: {}'.format(e))
|
||||
logger.error('Unsubscribe msg error: {}'.format(e))
|
||||
|
||||
def retry(self, _next, error, complete):
|
||||
logger.info('Retry subscribe channel: {}'.format(self.ch))
|
||||
|
||||
@@ -98,7 +98,7 @@ def ssh_private_key_gen(private_key, password=None):
|
||||
|
||||
def ssh_pubkey_gen(private_key=None, username='jumpserver', hostname='localhost', password=None):
|
||||
private_key = ssh_private_key_gen(private_key, password=password)
|
||||
if not isinstance(private_key, _supported_paramiko_ssh_key_types):
|
||||
if not isinstance(private_key, (paramiko.RSAKey, paramiko.DSSKey)):
|
||||
raise IOError('Invalid private key')
|
||||
|
||||
public_key = "%(key_type)s %(key_content)s %(username)s@%(hostname)s" % {
|
||||
@@ -274,4 +274,4 @@ def ensure_last_char_is_ascii(data):
|
||||
def data_to_json(data, sort_keys=True, indent=2, cls=None):
|
||||
if cls is None:
|
||||
cls = DjangoJSONEncoder
|
||||
return json.dumps(data, ensure_ascii=False, sort_keys=sort_keys, indent=indent, cls=cls)
|
||||
return json.dumps(data, sort_keys=sort_keys, indent=indent, cls=cls)
|
||||
|
||||
@@ -35,10 +35,7 @@ def i18n_trans(s):
|
||||
tpl, args = s.split(' % ', 1)
|
||||
args = args.split(', ')
|
||||
args = [gettext(arg) for arg in args]
|
||||
try:
|
||||
return gettext(tpl) % tuple(args)
|
||||
except TypeError:
|
||||
return gettext(tpl)
|
||||
return gettext(tpl) % tuple(args)
|
||||
|
||||
|
||||
def hello():
|
||||
|
||||
@@ -2,15 +2,12 @@
|
||||
#
|
||||
import re
|
||||
|
||||
import phonenumbers
|
||||
|
||||
from django.core.validators import RegexValidator
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
from rest_framework.validators import (
|
||||
UniqueTogetherValidator, ValidationError
|
||||
)
|
||||
from rest_framework import serializers
|
||||
from phonenumbers.phonenumberutil import NumberParseException
|
||||
|
||||
from common.utils.strings import no_special_chars
|
||||
|
||||
@@ -45,14 +42,9 @@ class NoSpecialChars:
|
||||
|
||||
|
||||
class PhoneValidator:
|
||||
pattern = re.compile(r"^1[3456789]\d{9}$")
|
||||
message = _('The mobile phone number format is incorrect')
|
||||
|
||||
def __call__(self, value):
|
||||
try:
|
||||
phone = phonenumbers.parse(value, 'CN')
|
||||
valid = phonenumbers.is_valid_number(phone)
|
||||
except NumberParseException:
|
||||
valid = False
|
||||
|
||||
if not valid:
|
||||
if not self.pattern.match(value):
|
||||
raise serializers.ValidationError(self.message)
|
||||
|
||||
@@ -214,7 +214,7 @@ class Config(dict):
|
||||
'REDIS_DB_WS': 6,
|
||||
|
||||
'GLOBAL_ORG_DISPLAY_NAME': '',
|
||||
'SITE_URL': 'http://127.0.0.1',
|
||||
'SITE_URL': 'http://localhost:8080',
|
||||
'USER_GUIDE_URL': '',
|
||||
'ANNOUNCEMENT_ENABLED': True,
|
||||
'ANNOUNCEMENT': {},
|
||||
@@ -376,7 +376,6 @@ class Config(dict):
|
||||
'AUTH_FEISHU': False,
|
||||
'FEISHU_APP_ID': '',
|
||||
'FEISHU_APP_SECRET': '',
|
||||
'FEISHU_VERSION': 'feishu',
|
||||
|
||||
'LOGIN_REDIRECT_TO_BACKEND': '', # 'OPENID / CAS / SAML2
|
||||
'LOGIN_REDIRECT_MSG_ENABLED': True,
|
||||
|
||||
@@ -20,7 +20,7 @@ default_context = {
|
||||
'LOGIN_WECOM_logo_logout': static('img/login_wecom_logo.png'),
|
||||
'LOGIN_DINGTALK_logo_logout': static('img/login_dingtalk_logo.png'),
|
||||
'LOGIN_FEISHU_logo_logout': static('img/login_feishu_logo.png'),
|
||||
'COPYRIGHT': 'FIT2CLOUD 飞致云' + ' © 2014-2023',
|
||||
'COPYRIGHT': 'FIT2CLOUD 飞致云' + ' © 2014-2022',
|
||||
'INTERFACE': default_interface,
|
||||
}
|
||||
|
||||
|
||||
@@ -137,7 +137,6 @@ DINGTALK_APPSECRET = CONFIG.DINGTALK_APPSECRET
|
||||
AUTH_FEISHU = CONFIG.AUTH_FEISHU
|
||||
FEISHU_APP_ID = CONFIG.FEISHU_APP_ID
|
||||
FEISHU_APP_SECRET = CONFIG.FEISHU_APP_SECRET
|
||||
FEISHU_VERSION = CONFIG.FEISHU_VERSION
|
||||
|
||||
# Saml2 auth
|
||||
AUTH_SAML2 = CONFIG.AUTH_SAML2
|
||||
|
||||
@@ -1,11 +1,10 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
#
|
||||
from datetime import datetime
|
||||
from functools import partial
|
||||
from werkzeug.local import LocalProxy
|
||||
from datetime import datetime
|
||||
|
||||
from django.conf import settings
|
||||
from werkzeug.local import LocalProxy
|
||||
|
||||
from common.local import thread_local
|
||||
|
||||
|
||||
@@ -35,7 +34,7 @@ def get_xpack_license_info() -> dict:
|
||||
corporation = info.get('corporation', '')
|
||||
else:
|
||||
current_year = datetime.now().year
|
||||
corporation = f'FIT2CLOUD 飞致云 © 2014-{current_year}'
|
||||
corporation = f'Copyright - FIT2CLOUD 飞致云 © 2014-{current_year}'
|
||||
info = {
|
||||
'corporation': corporation
|
||||
}
|
||||
|
||||
@@ -1,3 +1,3 @@
|
||||
version https://git-lfs.github.com/spec/v1
|
||||
oid sha256:6fa80b59b9b5f95a9cfcad8ec47eacd519bb962d139ab90463795a7b306a0a72
|
||||
size 137935
|
||||
oid sha256:8c2600b7094db2a9e64862169ff1c826d5064fae9b9e71744545a1cea88cbc65
|
||||
size 136280
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@@ -1,3 +1,3 @@
|
||||
version https://git-lfs.github.com/spec/v1
|
||||
oid sha256:9819889a6d8b2934b06c5b242e3f63f404997f30851919247a405f542e8a03bc
|
||||
size 113244
|
||||
oid sha256:a29193d2982b254444285cfb2d61f7ef7355ae2bab181cdf366446e879ab32fb
|
||||
size 111963
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@@ -17,7 +17,7 @@ class JMSInventory:
|
||||
:param account_policy: privileged_only, privileged_first, skip
|
||||
"""
|
||||
self.assets = self.clean_assets(assets)
|
||||
self.account_prefer = self.get_account_prefer(account_prefer)
|
||||
self.account_prefer = account_prefer
|
||||
self.account_policy = account_policy
|
||||
self.host_callback = host_callback
|
||||
self.exclude_hosts = {}
|
||||
@@ -139,47 +139,37 @@ class JMSInventory:
|
||||
self.make_ssh_account_vars(host, asset, account, automation, protocols, platform, gateway)
|
||||
return host
|
||||
|
||||
def get_asset_sorted_accounts(self, asset):
|
||||
accounts = list(asset.accounts.filter(is_active=True))
|
||||
connectivity_score = {'ok': 2, '-': 1, 'err': 0}
|
||||
sort_key = lambda x: (x.privileged, connectivity_score.get(x.connectivity, 0), x.date_updated)
|
||||
accounts_sorted = sorted(accounts, key=sort_key, reverse=True)
|
||||
return accounts_sorted
|
||||
|
||||
@staticmethod
|
||||
def get_account_prefer(account_prefer):
|
||||
account_usernames = []
|
||||
if isinstance(account_prefer, str) and account_prefer:
|
||||
account_usernames = list(map(lambda x: x.lower(), account_prefer.split(',')))
|
||||
return account_usernames
|
||||
|
||||
def get_refer_account(self, accounts):
|
||||
account = None
|
||||
if accounts:
|
||||
account = list(filter(
|
||||
lambda a: a.username.lower() in self.account_prefer, accounts
|
||||
))
|
||||
account = account[0] if account else None
|
||||
return account
|
||||
def get_asset_accounts(self, asset):
|
||||
return list(asset.accounts.filter(is_active=True))
|
||||
|
||||
def select_account(self, asset):
|
||||
accounts = self.get_asset_sorted_accounts(asset)
|
||||
accounts = self.get_asset_accounts(asset)
|
||||
if not accounts:
|
||||
return None
|
||||
account_selected = None
|
||||
account_usernames = self.account_prefer
|
||||
|
||||
refer_account = self.get_refer_account(accounts)
|
||||
if refer_account:
|
||||
return refer_account
|
||||
if isinstance(self.account_prefer, str):
|
||||
account_usernames = self.account_prefer.split(',')
|
||||
|
||||
account_selected = accounts[0]
|
||||
if self.account_policy == 'skip':
|
||||
return None
|
||||
elif self.account_policy == 'privileged_first':
|
||||
# 优先使用提供的名称
|
||||
if account_usernames:
|
||||
account_matched = list(filter(lambda account: account.username in account_usernames, accounts))
|
||||
account_selected = account_matched[0] if account_matched else None
|
||||
|
||||
if account_selected or self.account_policy == 'skip':
|
||||
return account_selected
|
||||
elif self.account_policy == 'privileged_only' and account_selected.privileged:
|
||||
|
||||
if self.account_policy in ['privileged_only', 'privileged_first']:
|
||||
account_matched = list(filter(lambda account: account.privileged, accounts))
|
||||
account_selected = account_matched[0] if account_matched else None
|
||||
|
||||
if account_selected:
|
||||
return account_selected
|
||||
else:
|
||||
return None
|
||||
|
||||
if self.account_policy == 'privileged_first':
|
||||
account_selected = accounts[0] if accounts else None
|
||||
return account_selected
|
||||
|
||||
def generate(self, path_dir):
|
||||
hosts = []
|
||||
|
||||
@@ -83,7 +83,7 @@ class CeleryResultApi(generics.RetrieveAPIView):
|
||||
|
||||
def get_object(self):
|
||||
pk = self.kwargs.get('pk')
|
||||
return AsyncResult(str(pk))
|
||||
return AsyncResult(pk)
|
||||
|
||||
|
||||
class CeleryPeriodTaskViewSet(CommonApiMixin, viewsets.ModelViewSet):
|
||||
|
||||
@@ -32,15 +32,6 @@ class PlaybookViewSet(OrgBulkModelViewSet):
|
||||
model = Playbook
|
||||
search_fields = ('name', 'comment')
|
||||
|
||||
def perform_destroy(self, instance):
|
||||
instance = self.get_object()
|
||||
if instance.job_set.exists():
|
||||
raise JMSException(code='playbook_has_job', detail={"msg": _("Currently playbook is being used in a job")})
|
||||
instance_id = instance.id
|
||||
super().perform_destroy(instance)
|
||||
dest_path = os.path.join(settings.DATA_DIR, "ops", "playbook", instance_id.__str__())
|
||||
shutil.rmtree(dest_path)
|
||||
|
||||
def get_queryset(self):
|
||||
queryset = super().get_queryset()
|
||||
queryset = queryset.filter(creator=self.request.user)
|
||||
@@ -71,10 +62,10 @@ class PlaybookFileBrowserAPIView(APIView):
|
||||
rbac_perms = ()
|
||||
permission_classes = (RBACPermission,)
|
||||
rbac_perms = {
|
||||
'GET': 'ops.change_playbook',
|
||||
'POST': 'ops.change_playbook',
|
||||
'DELETE': 'ops.change_playbook',
|
||||
'PATCH': 'ops.change_playbook',
|
||||
'GET': 'ops.change_playbooks',
|
||||
'POST': 'ops.change_playbooks',
|
||||
'DELETE': 'ops.change_playbooks',
|
||||
'PATCH': 'ops.change_playbooks',
|
||||
}
|
||||
protected_files = ['root', 'main.yml']
|
||||
|
||||
|
||||
@@ -46,9 +46,8 @@ class JMSPermedInventory(JMSInventory):
|
||||
self.user = user
|
||||
self.assets_accounts_mapper = self.get_assets_accounts_mapper()
|
||||
|
||||
def get_asset_sorted_accounts(self, asset):
|
||||
accounts = self.assets_accounts_mapper.get(asset.id, [])
|
||||
return list(accounts)
|
||||
def get_asset_accounts(self, asset):
|
||||
return self.assets_accounts_mapper.get(asset.id, [])
|
||||
|
||||
def get_assets_accounts_mapper(self):
|
||||
mapper = defaultdict(set)
|
||||
|
||||
@@ -13,7 +13,7 @@ class CeleryTaskLogView(PermissionsMixin, TemplateView):
|
||||
template_name = 'ops/celery_task_log.html'
|
||||
permission_classes = [RBACPermission]
|
||||
rbac_perms = {
|
||||
'GET': 'ops.view_celerytaskexecution'
|
||||
'GET': 'ops.view_celerytask'
|
||||
}
|
||||
|
||||
def get_context_data(self, **kwargs):
|
||||
|
||||
@@ -23,7 +23,6 @@ def migrate_app_perms_to_assets(apps, schema_editor):
|
||||
asset_permission = asset_permission_model()
|
||||
for attr in attrs:
|
||||
setattr(asset_permission, attr, getattr(app_perm, attr))
|
||||
asset_permission.name = f"App-{app_perm.name}"
|
||||
asset_permissions.append(asset_permission)
|
||||
asset_permission_model.objects.bulk_create(asset_permissions, ignore_conflicts=True)
|
||||
|
||||
|
||||
@@ -9,11 +9,11 @@ def migrate_system_user_to_accounts(apps, schema_editor):
|
||||
bulk_size = 10000
|
||||
while True:
|
||||
asset_permissions = asset_permission_model.objects \
|
||||
.prefetch_related('system_users')[count:bulk_size]
|
||||
.prefetch_related('system_users')[count:bulk_size]
|
||||
if not asset_permissions:
|
||||
break
|
||||
|
||||
count += len(asset_permissions)
|
||||
|
||||
updated = []
|
||||
for asset_permission in asset_permissions:
|
||||
asset_permission.accounts = [s.username for s in asset_permission.system_users.all()]
|
||||
|
||||
@@ -1,11 +1,10 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
#
|
||||
|
||||
from django.db.models import Q
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
from rest_framework import serializers
|
||||
|
||||
from accounts.models import AccountTemplate, Account
|
||||
from accounts.tasks import push_accounts_to_assets_task
|
||||
from assets.models import Asset, Node
|
||||
from common.serializers.fields import BitChoicesField, ObjectRelatedField
|
||||
from orgs.mixins.serializers import BulkOrgResourceModelSerializer
|
||||
@@ -19,12 +18,6 @@ class ActionChoicesField(BitChoicesField):
|
||||
def __init__(self, **kwargs):
|
||||
super().__init__(choice_cls=ActionChoices, **kwargs)
|
||||
|
||||
def to_file_representation(self, value):
|
||||
return [v['value'] for v in value]
|
||||
|
||||
def to_file_internal_value(self, data):
|
||||
return data
|
||||
|
||||
|
||||
class AssetPermissionSerializer(BulkOrgResourceModelSerializer):
|
||||
users = ObjectRelatedField(queryset=User.objects, many=True, required=False, label=_('User'))
|
||||
@@ -38,8 +31,6 @@ class AssetPermissionSerializer(BulkOrgResourceModelSerializer):
|
||||
is_expired = serializers.BooleanField(read_only=True, label=_("Is expired"))
|
||||
accounts = serializers.ListField(label=_("Account"), required=False)
|
||||
|
||||
template_accounts = AccountTemplate.objects.none()
|
||||
|
||||
class Meta:
|
||||
model = AssetPermission
|
||||
fields_mini = ["id", "name"]
|
||||
@@ -82,58 +73,8 @@ class AssetPermissionSerializer(BulkOrgResourceModelSerializer):
|
||||
actions.default = list(actions.choices.keys())
|
||||
|
||||
@staticmethod
|
||||
def get_all_assets(nodes, assets):
|
||||
node_asset_ids = Node.get_nodes_all_assets(*nodes).values_list('id', flat=True)
|
||||
direct_asset_ids = [asset.id for asset in assets]
|
||||
asset_ids = set(direct_asset_ids + list(node_asset_ids))
|
||||
return Asset.objects.filter(id__in=asset_ids)
|
||||
|
||||
def create_accounts(self, assets):
|
||||
need_create_accounts = []
|
||||
account_attribute = [
|
||||
'name', 'username', 'secret_type', 'secret', 'privileged', 'is_active', 'org_id'
|
||||
]
|
||||
for asset in assets:
|
||||
asset_exist_accounts = Account.objects.none()
|
||||
for template in self.template_accounts:
|
||||
asset_exist_accounts |= asset.accounts.filter(
|
||||
username=template.username,
|
||||
secret_type=template.secret_type,
|
||||
)
|
||||
username_secret_type_dict = asset_exist_accounts.values('username', 'secret_type')
|
||||
for template in self.template_accounts:
|
||||
condition = {
|
||||
'username': template.username,
|
||||
'secret_type': template.secret_type
|
||||
}
|
||||
if condition in username_secret_type_dict:
|
||||
continue
|
||||
account_data = {key: getattr(template, key) for key in account_attribute}
|
||||
account_data['name'] = f"{account_data['name']}-clone"
|
||||
need_create_accounts.append(Account(**{'asset_id': asset.id, **account_data}))
|
||||
return Account.objects.bulk_create(need_create_accounts)
|
||||
|
||||
def create_and_push_account(self, nodes, assets):
|
||||
if not self.template_accounts:
|
||||
return
|
||||
assets = self.get_all_assets(nodes, assets)
|
||||
accounts = self.create_accounts(assets)
|
||||
account_ids = [str(account.id) for account in accounts]
|
||||
slice_count = 20
|
||||
for i in range(0, len(account_ids), slice_count):
|
||||
push_accounts_to_assets_task.delay(account_ids[i:i + slice_count])
|
||||
|
||||
def validate_accounts(self, usernames: list[str]):
|
||||
template_ids = []
|
||||
account_usernames = []
|
||||
for username in usernames:
|
||||
if username.startswith('%'):
|
||||
template_ids.append(username[1:])
|
||||
else:
|
||||
account_usernames.append(username)
|
||||
self.template_accounts = AccountTemplate.objects.filter(id__in=template_ids)
|
||||
template_usernames = list(self.template_accounts.values_list('username', flat=True))
|
||||
return list(set(account_usernames + template_usernames))
|
||||
def validate_accounts(accounts):
|
||||
return list(set(accounts))
|
||||
|
||||
@classmethod
|
||||
def setup_eager_loading(cls, queryset):
|
||||
@@ -171,13 +112,6 @@ class AssetPermissionSerializer(BulkOrgResourceModelSerializer):
|
||||
).distinct()
|
||||
instance.nodes.add(*nodes_to_set)
|
||||
|
||||
def validate(self, attrs):
|
||||
self.create_and_push_account(
|
||||
attrs.get("nodes", []),
|
||||
attrs.get("assets", [])
|
||||
)
|
||||
return super().validate(attrs)
|
||||
|
||||
def create(self, validated_data):
|
||||
display = {
|
||||
"users_display": validated_data.pop("users_display", ""),
|
||||
|
||||
@@ -22,7 +22,6 @@ user_perms = (
|
||||
("ops", "playbook", "*", "*"),
|
||||
("ops", "job", "*", "*"),
|
||||
("ops", "jobexecution", "*", "*"),
|
||||
("ops", "celerytaskexecution", "view", "*"),
|
||||
)
|
||||
|
||||
system_user_perms = (
|
||||
|
||||
@@ -135,7 +135,7 @@ only_system_permissions = (
|
||||
('xpack', 'license', '*', '*'),
|
||||
('settings', 'setting', '*', '*'),
|
||||
('tickets', '*', '*', '*'),
|
||||
('ops', 'celerytask', 'view', 'taskmonitor'),
|
||||
('ops', 'task', 'view', 'taskmonitor'),
|
||||
('terminal', 'terminal', '*', '*'),
|
||||
('terminal', 'commandstorage', '*', '*'),
|
||||
('terminal', 'replaystorage', '*', '*'),
|
||||
|
||||
@@ -42,7 +42,7 @@ class MailTestingAPI(APIView):
|
||||
# if k.startswith('EMAIL'):
|
||||
# setattr(settings, k, v)
|
||||
try:
|
||||
subject = settings.EMAIL_SUBJECT_PREFIX or '' + "Test"
|
||||
subject = settings.EMAIL_SUBJECT_PREFIX + "Test"
|
||||
message = "Test smtp setting"
|
||||
email_from = email_from or email_host_user
|
||||
email_recipient = email_recipient or email_from
|
||||
|
||||
@@ -9,13 +9,6 @@ __all__ = ['FeiShuSettingSerializer']
|
||||
class FeiShuSettingSerializer(serializers.Serializer):
|
||||
PREFIX_TITLE = _('FeiShu')
|
||||
|
||||
VERSION_CHOICES = (
|
||||
('feishu', _('FeiShu')),
|
||||
('lark', 'Lark')
|
||||
)
|
||||
AUTH_FEISHU = serializers.BooleanField(default=False, label=_('Enable FeiShu Auth'))
|
||||
FEISHU_APP_ID = serializers.CharField(max_length=256, required=True, label='App ID')
|
||||
FEISHU_APP_SECRET = EncryptedField(max_length=256, required=False, label='App Secret')
|
||||
FEISHU_VERSION = serializers.ChoiceField(
|
||||
choices=VERSION_CHOICES, default='feishu', label=_('Version')
|
||||
)
|
||||
AUTH_FEISHU = serializers.BooleanField(default=False, label=_('Enable FeiShu Auth'))
|
||||
|
||||
@@ -74,9 +74,9 @@ class LDAPSettingSerializer(serializers.Serializer):
|
||||
)
|
||||
AUTH_LDAP_CONNECT_TIMEOUT = serializers.IntegerField(
|
||||
min_value=1, max_value=300,
|
||||
required=False, label=_('Connect timeout (s)'),
|
||||
required=False, label=_('Connect timeout'),
|
||||
)
|
||||
AUTH_LDAP_SEARCH_PAGED_SIZE = serializers.IntegerField(required=False, label=_('Search paged size (piece)'))
|
||||
AUTH_LDAP_SEARCH_PAGED_SIZE = serializers.IntegerField(required=False, label=_('Search paged size'))
|
||||
|
||||
AUTH_LDAP = serializers.BooleanField(required=False, label=_('Enable LDAP auth'))
|
||||
|
||||
|
||||
@@ -87,7 +87,7 @@ class OIDCSettingSerializer(KeycloakSettingSerializer):
|
||||
)
|
||||
AUTH_OPENID_SCOPES = serializers.CharField(required=False, max_length=1024, label=_('Scopes'))
|
||||
AUTH_OPENID_ID_TOKEN_MAX_AGE = serializers.IntegerField(
|
||||
required=False, label=_('Id token max age (s)')
|
||||
required=False, label=_('Id token max age')
|
||||
)
|
||||
AUTH_OPENID_ID_TOKEN_INCLUDE_CLAIMS = serializers.BooleanField(
|
||||
required=False, label=_('Id token include claims')
|
||||
|
||||
@@ -1,9 +1,9 @@
|
||||
# coding: utf-8
|
||||
#
|
||||
#
|
||||
from celery import shared_task
|
||||
from django.conf import settings
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
from django.db import transaction
|
||||
|
||||
from common.utils import get_logger
|
||||
from ops.celery.decorator import after_app_ready_start
|
||||
from ops.celery.utils import (
|
||||
@@ -22,7 +22,6 @@ def sync_ldap_user():
|
||||
|
||||
|
||||
@shared_task(verbose_name=_('Import ldap user'))
|
||||
@transaction.atomic
|
||||
def import_ldap_user():
|
||||
logger.info("Start import ldap user task")
|
||||
util_server = LDAPServerUtil()
|
||||
|
||||
@@ -18,10 +18,6 @@
|
||||
margin: 0 auto;
|
||||
padding: 100px 20px 20px 20px;
|
||||
}
|
||||
|
||||
.ibox-content {
|
||||
padding: 30px;
|
||||
}
|
||||
</style>
|
||||
{% block custom_head_css_js %} {% endblock %}
|
||||
</head>
|
||||
@@ -34,7 +30,7 @@
|
||||
<h2 class="font-bold">
|
||||
{% block title %}{% endblock %}
|
||||
</h2>
|
||||
<div style="margin: 20px 0 0 0">
|
||||
<div style="margin: 10px 0">
|
||||
{% block content %} {% endblock %}
|
||||
</div>
|
||||
</div>
|
||||
|
||||
@@ -23,7 +23,7 @@
|
||||
|
||||
<div class="row">
|
||||
{% if has_cancel %}
|
||||
<div class="col-sm-3">
|
||||
<div class="col-sm-3">
|
||||
<a href="{{ cancel_url }}" class="btn btn-default block full-width m-b">
|
||||
{% trans 'Cancel' %}
|
||||
</a>
|
||||
@@ -43,7 +43,7 @@
|
||||
{% endblock %}
|
||||
|
||||
{% block custom_foot_js %}
|
||||
<script>
|
||||
<script>
|
||||
var message = ''
|
||||
var time = '{{ interval }}'
|
||||
{% if error %}
|
||||
|
||||
@@ -3,12 +3,11 @@
|
||||
- hosts: all
|
||||
vars:
|
||||
APPLET_DOWNLOAD_HOST: https://demo.jumpserver.org
|
||||
IGNORE_VERIFY_CERTS: true
|
||||
HOST_NAME: test
|
||||
HOST_ID: 00000000-0000-0000-0000-000000000000
|
||||
CORE_HOST: https://demo.jumpserver.org
|
||||
BOOTSTRAP_TOKEN: PleaseChangeMe
|
||||
RDS_Licensing: false
|
||||
RDS_Licensing: true
|
||||
RDS_LicenseServer: 127.0.0.1
|
||||
RDS_LicensingMode: 4
|
||||
RDS_fSingleSessionPerUser: 1
|
||||
@@ -17,6 +16,13 @@
|
||||
TinkerInstaller: Tinker_Installer.exe
|
||||
|
||||
tasks:
|
||||
- name: Install RDS-Licensing (RDS)
|
||||
ansible.windows.win_feature:
|
||||
name: RDS-Licensing
|
||||
state: present
|
||||
include_management_tools: yes
|
||||
when: RDS_Licensing
|
||||
|
||||
- name: Install RDS-RD-Server (RDS)
|
||||
ansible.windows.win_feature:
|
||||
name: RDS-RD-Server
|
||||
@@ -38,7 +44,6 @@
|
||||
ansible.windows.win_get_url:
|
||||
url: "{{ APPLET_DOWNLOAD_HOST }}/download/applets/{{ TinkerInstaller }}"
|
||||
dest: "{{ ansible_env.TEMP }}\\{{ TinkerInstaller }}"
|
||||
validate_certs: "{{ not IGNORE_VERIFY_CERTS }}"
|
||||
|
||||
- name: Install JumpServer Tinker (jumpserver)
|
||||
ansible.windows.win_package:
|
||||
@@ -59,7 +64,6 @@
|
||||
ansible.windows.win_get_url:
|
||||
url: "{{ APPLET_DOWNLOAD_HOST }}/download/applets/python-3.10.8-amd64.exe"
|
||||
dest: "{{ ansible_env.TEMP }}\\python-3.10.8-amd64.exe"
|
||||
validate_certs: "{{ not IGNORE_VERIFY_CERTS }}"
|
||||
|
||||
- name: Install the python-3.10.8
|
||||
ansible.windows.win_package:
|
||||
@@ -74,23 +78,11 @@
|
||||
state: present
|
||||
register: win_install_python
|
||||
|
||||
- name: Check pip command exists
|
||||
ansible.windows.win_powershell:
|
||||
script: |
|
||||
if (Get-Command -Name 'pip' -ErrorAction SilentlyContinue) {
|
||||
$Ansible.Changed = $false
|
||||
}
|
||||
else {
|
||||
$Ansible.Changed = $true
|
||||
}
|
||||
register: check_pip_command
|
||||
ignore_errors: yes
|
||||
|
||||
- name: Reboot if installing requires it
|
||||
ansible.windows.win_reboot:
|
||||
post_reboot_delay: 10
|
||||
test_command: whoami
|
||||
when: check_pip_command.changed or rds_install.reboot_required or win_install_python.reboot_required
|
||||
when: rds_install.reboot_required or win_install_python.reboot_required
|
||||
|
||||
- name: Set RDS LicenseServer (regedit)
|
||||
ansible.windows.win_regedit:
|
||||
@@ -98,7 +90,6 @@
|
||||
name: LicenseServers
|
||||
data: "{{ RDS_LicenseServer }}"
|
||||
type: string
|
||||
when: RDS_Licensing
|
||||
|
||||
- name: Set RDS LicensingMode (regedit)
|
||||
ansible.windows.win_regedit:
|
||||
@@ -106,7 +97,6 @@
|
||||
name: LicensingMode
|
||||
data: "{{ RDS_LicensingMode }}"
|
||||
type: dword
|
||||
when: RDS_Licensing
|
||||
|
||||
- name: Set RDS fSingleSessionPerUser (regedit)
|
||||
ansible.windows.win_regedit:
|
||||
@@ -114,7 +104,6 @@
|
||||
name: fSingleSessionPerUser
|
||||
data: "{{ RDS_fSingleSessionPerUser }}"
|
||||
type: dword
|
||||
when: RDS_Licensing
|
||||
|
||||
- name: Set RDS MaxDisconnectionTime (regedit)
|
||||
ansible.windows.win_regedit:
|
||||
@@ -135,7 +124,6 @@
|
||||
ansible.windows.win_get_url:
|
||||
url: "{{ APPLET_DOWNLOAD_HOST }}/download/applets/pip_packages.zip"
|
||||
dest: "{{ ansible_env.TEMP }}\\pip_packages.zip"
|
||||
validate_certs: "{{ not IGNORE_VERIFY_CERTS }}"
|
||||
|
||||
- name: Unzip pip_packages
|
||||
community.windows.win_unzip:
|
||||
@@ -151,7 +139,6 @@
|
||||
ansible.windows.win_get_url:
|
||||
url: "{{ APPLET_DOWNLOAD_HOST }}/download/applets/chromedriver_win32.zip"
|
||||
dest: "{{ ansible_env.TEMP }}\\chromedriver_win32.zip"
|
||||
validate_certs: "{{ not IGNORE_VERIFY_CERTS }}"
|
||||
|
||||
- name: Unzip chromedriver (Chromium)
|
||||
community.windows.win_unzip:
|
||||
@@ -162,7 +149,6 @@
|
||||
ansible.windows.win_get_url:
|
||||
url: "{{ APPLET_DOWNLOAD_HOST }}/download/applets/chrome-win.zip"
|
||||
dest: "{{ ansible_env.TEMP }}\\chrome-win.zip"
|
||||
validate_certs: "{{ not IGNORE_VERIFY_CERTS }}"
|
||||
|
||||
- name: Unzip Chromium (Chromium)
|
||||
community.windows.win_unzip:
|
||||
@@ -175,7 +161,7 @@
|
||||
- 'C:\Program Files\Chrome\chrome-win'
|
||||
- 'C:\Program Files\JumpServer\drivers\chromedriver_win32'
|
||||
|
||||
- name: Set Chromium variables disable Google Api (Chromium)
|
||||
- name: Set Chromium variables diable Google Api (Chromium)
|
||||
ansible.windows.win_environment:
|
||||
level: machine
|
||||
variables:
|
||||
@@ -187,7 +173,6 @@
|
||||
ansible.windows.win_get_url:
|
||||
url: "{{ APPLET_DOWNLOAD_HOST }}/download/applets/navicat161_premium_en_x64.exe"
|
||||
dest: "{{ ansible_env.TEMP }}\\navicat161_premium_en_x64.exe"
|
||||
validate_certs: "{{ not IGNORE_VERIFY_CERTS }}"
|
||||
|
||||
- name: Install navicat (navicat)
|
||||
ansible.windows.win_package:
|
||||
@@ -198,8 +183,8 @@
|
||||
|
||||
- name: Generate tinkerd component config
|
||||
ansible.windows.win_shell:
|
||||
"tinkerd config --hostname {{ HOST_NAME }} --core_host {{ CORE_HOST }}
|
||||
--token {{ BOOTSTRAP_TOKEN }} --host_id {{ HOST_ID }} --ignore-verify-certs {{ IGNORE_VERIFY_CERTS }}"
|
||||
"tinkerd config --hostname {{ HOST_NAME }} --core_host {{ CORE_HOST }}
|
||||
--token {{ BOOTSTRAP_TOKEN }} --host_id {{ HOST_ID }}"
|
||||
|
||||
- name: Install tinkerd service
|
||||
ansible.windows.win_shell:
|
||||
@@ -222,3 +207,4 @@
|
||||
- name: Sync all remote applets
|
||||
ansible.windows.win_shell:
|
||||
"tinkerd install all"
|
||||
|
||||
|
||||
@@ -105,13 +105,9 @@ class Session(OrgModelMixin):
|
||||
def find_ok_relative_path_in_storage(self, storage):
|
||||
session_paths = self.get_all_possible_relative_path()
|
||||
for rel_path in session_paths:
|
||||
# storage 为多个外部存储时, 可能会因部分不可用,
|
||||
# 抛出异常, 影响录像的获取
|
||||
try:
|
||||
if storage.exists(rel_path):
|
||||
return rel_path
|
||||
except:
|
||||
pass
|
||||
if storage.exists(rel_path):
|
||||
return rel_path
|
||||
|
||||
@property
|
||||
def asset_obj(self):
|
||||
return Asset.objects.get(id=self.asset_id)
|
||||
|
||||
@@ -29,18 +29,8 @@ class DeployOptionsSerializer(serializers.Serializer):
|
||||
(0, _("Enabled")),
|
||||
)
|
||||
|
||||
CORE_HOST = serializers.CharField(
|
||||
default=settings.SITE_URL, label=_('Core API'), max_length=1024,
|
||||
help_text=_("""
|
||||
Tips: The application release machine communicates with the Core service.
|
||||
If the release machine and the Core service are on the same network segment,
|
||||
it is recommended to fill in the intranet address, otherwise fill in the current site URL
|
||||
<br>
|
||||
eg: https://172.16.10.110 or https://dev.jumpserver.com
|
||||
""")
|
||||
)
|
||||
IGNORE_VERIFY_CERTS = serializers.BooleanField(default=True, label=_("Ignore Certificate Verification"))
|
||||
RDS_Licensing = serializers.BooleanField(default=False, label=_("Existing RDS license"))
|
||||
CORE_HOST = serializers.CharField(default=settings.SITE_URL, label=_('API Server'), max_length=1024)
|
||||
RDS_Licensing = serializers.BooleanField(default=False, label=_("RDS Licensing"))
|
||||
RDS_LicenseServer = serializers.CharField(default='127.0.0.1', label=_('RDS License Server'), max_length=1024)
|
||||
RDS_LicensingMode = serializers.ChoiceField(choices=LICENSE_MODE_CHOICES, default=2, label=_('RDS Licensing Mode'))
|
||||
RDS_fSingleSessionPerUser = serializers.ChoiceField(choices=SESSION_PER_USER, default=1,
|
||||
|
||||
@@ -3,7 +3,6 @@ from rest_framework import serializers
|
||||
|
||||
from acls.serializers.rules import ip_group_child_validator, ip_group_help_text
|
||||
from common.serializers import BulkModelSerializer
|
||||
from common.serializers.fields import ObjectRelatedField
|
||||
from ..models import Endpoint, EndpointRule
|
||||
from ..utils import db_port_manager
|
||||
|
||||
@@ -33,7 +32,7 @@ class EndpointSerializer(BulkModelSerializer):
|
||||
'comment', 'date_created', 'date_updated', 'created_by'
|
||||
]
|
||||
extra_kwargs = {
|
||||
'host': {'help_text': _('Visit IP/Host, if empty, use the current request instead')},
|
||||
'host': {'help_text': 'Visit IP/host, if empty, use the current request instead'},
|
||||
}
|
||||
|
||||
def get_oracle_port(self, obj: Endpoint):
|
||||
@@ -62,15 +61,13 @@ class EndpointRuleSerializer(BulkModelSerializer):
|
||||
default=['*'], label=_('IP'), help_text=_ip_group_help_text,
|
||||
child=serializers.CharField(max_length=1024, validators=[ip_group_child_validator])
|
||||
)
|
||||
endpoint = ObjectRelatedField(
|
||||
allow_null=True, required=False, queryset=Endpoint.objects, label=_('Endpoint')
|
||||
)
|
||||
endpoint_display = serializers.ReadOnlyField(source='endpoint.name', label=_('Endpoint'))
|
||||
|
||||
class Meta:
|
||||
model = EndpointRule
|
||||
fields_mini = ['id', 'name']
|
||||
fields_small = fields_mini + ['ip_group', 'priority']
|
||||
fields_fk = ['endpoint']
|
||||
fields_fk = ['endpoint', 'endpoint_display']
|
||||
fields = fields_mini + fields_small + fields_fk + [
|
||||
'comment', 'date_created', 'date_updated', 'created_by'
|
||||
]
|
||||
|
||||
@@ -1,16 +1,12 @@
|
||||
# -*- coding: utf-8 -*-
|
||||
#
|
||||
import phonenumbers
|
||||
|
||||
from functools import partial
|
||||
|
||||
from django.utils.translation import ugettext_lazy as _
|
||||
from rest_framework import serializers
|
||||
|
||||
from common.serializers import CommonBulkSerializerMixin
|
||||
from common.serializers.fields import (
|
||||
EncryptedField, ObjectRelatedField, LabeledChoiceField, PhoneField
|
||||
)
|
||||
from common.serializers.fields import EncryptedField, ObjectRelatedField, LabeledChoiceField
|
||||
from common.utils import pretty_string, get_logger
|
||||
from common.validators import PhoneValidator
|
||||
from rbac.builtin import BuiltinRole
|
||||
@@ -85,8 +81,8 @@ class UserSerializer(RolesSerializerMixin, CommonBulkSerializerMixin, serializer
|
||||
password_strategy = LabeledChoiceField(
|
||||
choices=PasswordStrategy.choices,
|
||||
default=PasswordStrategy.email,
|
||||
allow_null=True,
|
||||
required=False,
|
||||
write_only=True,
|
||||
label=_("Password strategy"),
|
||||
)
|
||||
mfa_enabled = serializers.BooleanField(read_only=True, label=_("MFA enabled"))
|
||||
@@ -105,9 +101,6 @@ class UserSerializer(RolesSerializerMixin, CommonBulkSerializerMixin, serializer
|
||||
label=_("Password"), required=False, allow_blank=True,
|
||||
allow_null=True, max_length=1024,
|
||||
)
|
||||
phone = PhoneField(
|
||||
validators=[PhoneValidator()], required=False, allow_blank=True, allow_null=True, label=_("Phone")
|
||||
)
|
||||
custom_m2m_fields = {
|
||||
"system_roles": [BuiltinRole.system_user],
|
||||
"org_roles": [BuiltinRole.org_user],
|
||||
@@ -149,7 +142,6 @@ class UserSerializer(RolesSerializerMixin, CommonBulkSerializerMixin, serializer
|
||||
# 在serializer 上定义的字段
|
||||
fields_custom = ["login_blocked", "password_strategy"]
|
||||
fields = fields_verbose + fields_fk + fields_m2m + fields_custom
|
||||
fields_unexport = ["avatar_url", ]
|
||||
|
||||
read_only_fields = [
|
||||
"date_joined", "last_login", "created_by",
|
||||
@@ -174,7 +166,7 @@ class UserSerializer(RolesSerializerMixin, CommonBulkSerializerMixin, serializer
|
||||
"created_by": {"read_only": True, "allow_blank": True},
|
||||
"role": {"default": "User"},
|
||||
"is_otp_secret_key_bound": {"label": _("Is OTP bound")},
|
||||
'mfa_level': {'label': _("MFA level")},
|
||||
"phone": {"validators": [PhoneValidator()]},
|
||||
}
|
||||
|
||||
def validate_password(self, password):
|
||||
|
||||
@@ -58,7 +58,7 @@
|
||||
{% if not b.can_disable %} disabled {% endif %}
|
||||
onclick="goTo('{{ b.get_disable_url }}')"
|
||||
>
|
||||
{% trans 'Reset' %}
|
||||
{% trans 'Disable' %}
|
||||
</button>
|
||||
<span class="help-inline">{{ b.help_text_of_disable }}</span>
|
||||
{% else %}
|
||||
|
||||
@@ -29,7 +29,6 @@ pycparser==2.21
|
||||
cryptography==38.0.4
|
||||
pycryptodome==3.15.0
|
||||
pycryptodomex==3.15.0
|
||||
phonenumbers==8.13.8
|
||||
gmssl==3.2.1
|
||||
itsdangerous==1.1.0
|
||||
pyotp==2.6.0
|
||||
|
||||
Reference in New Issue
Block a user